AI SOC is an advanced security operations centre that uses artificial intelligence and machine learning to automate cyber threat detection, investigation, response and proactive hunting more efficiently than traditional SOCs.
With the rise of cyber threats and sophisticated attacks, traditional security measures are no longer enough. The need for fast and efficient responses to potential risks has led to the rise of AI-driven Security Operations Centres (SOCs).
According to Viscount Camrose, the UK government's Minister for AI and Intellectual Property, the UK AI market is predicted to grow to over $1 trillion by 2035. The UK government's DSIT reported that 68% of businesses surveyed currently use at least one AI technology, while 32% plan to adopt AI in the future.
AI-driven SOCs leverage artificial intelligence to enhance security measures, faster response times, and predictive analysis that can stop threats before they cause damage.
In this blog, we'll explore what AI-driven SOCs are, their benefits, and how they can help businesses stay ahead of security threats.
Key Takeaways:
-
AI-driven automation in security operation centres (SOCs) is the strategic integration of AI technologies to enhance and safeguard operational workflows within the SOC strategy.
-
Advantages of AI in SOC: Artificial Intelligence (AI) enhances SOC capabilities in detecting, analysing, and responding to threats.
-
The integration of AI-driven automation has significantly improved the SOC's ability to navigate and mitigate the evolving challenges posed by automated threats in contemporary cybersecurity.
Understanding the Role of AI in Cybersecurity
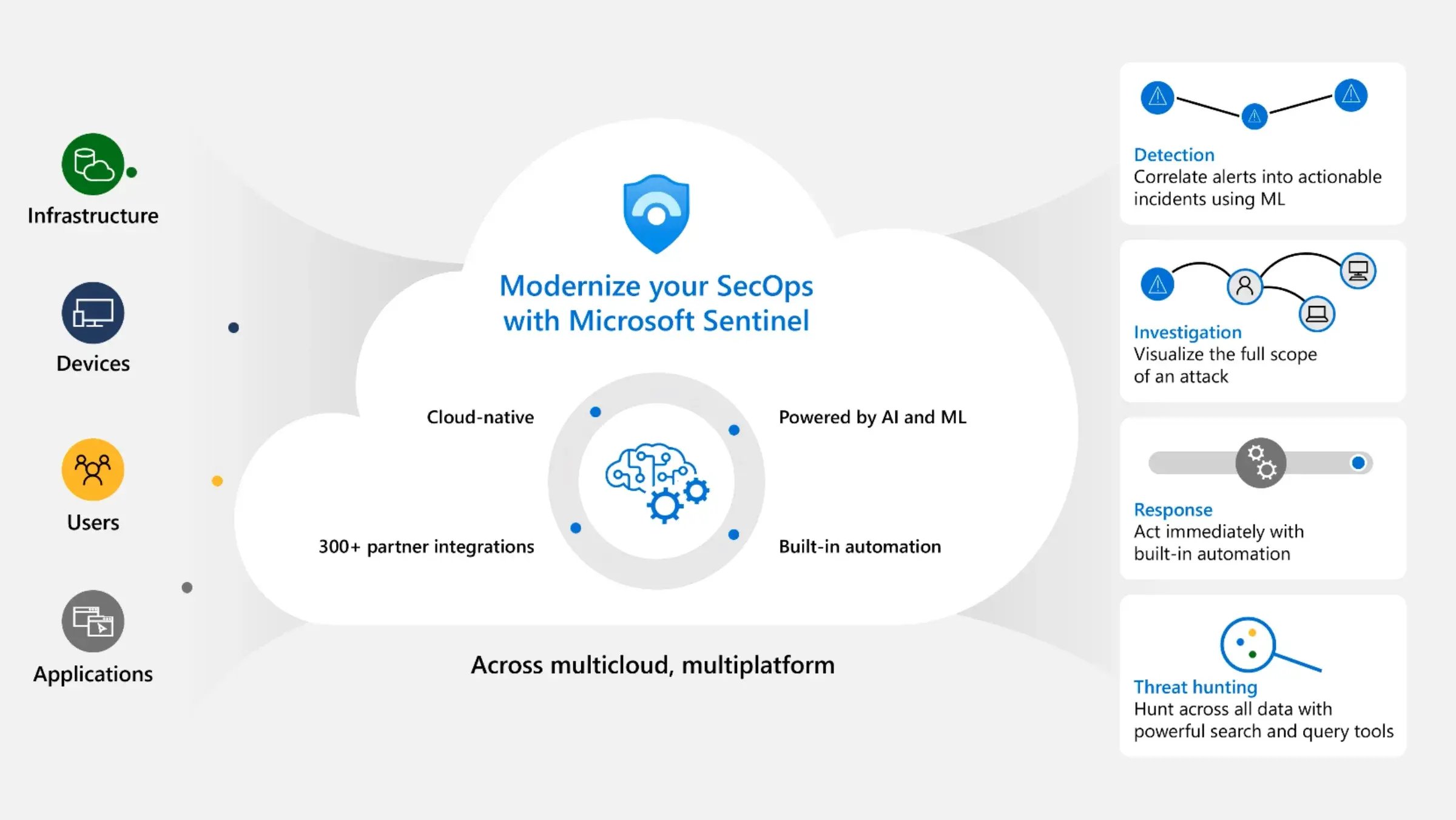 Source: Microsoft
Source: MicrosoftThe traditional SOC approach relies heavily on human intelligence to sift through alerts and events, which can lead to inefficiencies, especially with large volumes of data. Security practitioners often face alert fatigue, as a majority of these alerts may be false positives or low-risk events.
AI-assisted SOCs, on the other hand, can leverage AI and ML algorithms to continuously learn from past incidents, detect subtle patterns of malicious activity, and prioritise advanced threats more accurately.
In an AI-driven SOC, AI technologies improve threat detection by spotting irregularities that may be difficult for human analysts to recognise.
Moreover, AI-powered systems can accelerate the investigation and response process, offering actionable intelligence and automated decisions that help SOC analysts focus on high-impact security incidents.
Vijay Poloju, SOC Technical Lead at Aztech, highlights the key benefits of working with an AI-native security operations centre. It enables real-time detection of threats using deep learning and behavioural advanced analytics, allowing his team to proactively respond to incidents before they escalate. Automated SOC processes have streamlined incident management, freeing up time for strategic security investigations. Also, collaborating with skilled SOC teams enhances cross-functional communication, ensuring rapid threat mitigation. Learn More about the Aztech's SOC services.
What is an AI-Driven SOC?
An AI-driven SOC refers to a Security Operations Centre that uses artificial intelligence and machine learning to automate threat detection, analysis, and response.
When we add AI to security operations, we enhance the SOC’s ability to handle threats more efficiently. AI SOC architecture leverages machine learning, data analytics, and automation to help security teams detect and mitigate risks faster than ever before. AI helps the SOC become smarter by learning from past threats and predicting new ones.
In AI-assisted SOCs, advanced algorithms can quickly analyse large data sets, identify patterns, and recognise anomalies that could indicate a cyber threat. This allows businesses to respond to security incidents in real time, minimising the impact of cyberattacks.
Key Components of SOC Automation
AI-powered SOCs rely on several key components to operate effectively. These components work together to automate processes, improve detection capabilities, and respond to threats efficiently.
1. Threat Intelligence
Threat intelligence is data ingestion that provides insights into potential and active cyber threats. AI systems collect, analyse, and process this information to help detect emerging security threats.
2. Machine Learning Algorithms
ML allows the SOC to improve over time. As it analyses more threats and incidents, the AI system better recognises patterns and detects anomalies that may signal a potential attack.
3. Security Information and Event Management (SIEM)
SIEM systems collect and analyse data from various sources across an organisation's IT infrastructure. When integrated with AI, SIEM can detect threats in real time and trigger automatic responses.
4. Automated Incident Response Capabilities
AI-native SOCs are equipped with automated response systems that can immediately act when a threat is detected. This could involve isolating affected systems, blocking malicious IP addresses, or other predefined measures.
5. User and Entity Behaviour Analytics (UEBA)
User and entity behaviour analytics (UEBA) helps SOCs pinpoint insider threats or compromised accounts. By correlating this behavioural data with known threat patterns, AI can quickly identify and flag anomalous activities that may go unnoticed.
Top Benefits of AI-Driven Security Operations Centres (SOCs)
Organisations that integrate AI into their SOCs can expect several significant benefits. These advantages help improve SOC operations and enable faster, more effective responses to potential threats.
1. Faster Threat Detection
AI can analyse large amounts of security data in seconds, and perform threat investigation much faster than a human analyst could. This speed is essential for minimising the attack surface caused by cyberattacks.
2. Automated Response
With AI, many responses can be automated, reducing the time between detection and action. This helps contain threats more quickly, preventing them from spreading throughout the organisation.
3. Reduced Human Error
Human analysts are prone to fatigue and mistakes, especially when faced with repetitive tasks. AI-driven SOCs help eliminate this risk by automating those tasks and ensuring accuracy.
4. Cost Efficiency
AI reduces the need for a large team of SOC analysts by handling routine tasks and analysis. This results in lower operational costs while maintaining high levels of security.
5. Proactive Threat Hunting
AI-driven SOCs don’t just react to threats—they can predict them. Using AL and ML, the system can identify patterns and potential vulnerabilities, allowing the SOC to address risks before they are exploited.
6. 24/7 Monitoring and Consistency
AI never sleeps. It can monitor an organisation's infrastructure continuously, ensuring that threats are detected at any time of the day or night.
AI in Security Orchestration, Automation, and Response (SOAR)
Security Orchestration, Automation, and Response (SOAR) platforms play a crucial role in modern SOCs. These platforms integrate various security tools and data sources, allowing organisations to automate responses to security incidents.
Furthermore, AI enhances SOAR capabilities by enabling more advanced automation and orchestration.
For instance, AI can trigger automated playbooks for handling specific types of incidents, such as malware infections or data breaches.
By leveraging AI, SOAR platforms can process vast amounts of security data and take appropriate actions without human intervention, speeding up response times and reducing the likelihood of human error.
How AI-Powered SOCs Detect and Respond to Threats
One of the most critical functions of an AI-powered SOC is the ability to detect and respond to threats in real time. Here’s a closer look at how this process works:
1. Data Collection
The SOC collects vast amounts of data from different systems, such as network traffic, endpoint logs, and user activity.
2. Threat Detection
AI analyses this data using machine and deep learning algorithms to detect unusual patterns or anomalies that may indicate a threat. AI systems can spot minute deviations from normal behaviour, signalling potential risks.
3. Incident Prioritisation
Once a threat is identified, the AI-driven SOC assigns a priority level based on the severity of the risk. Critical threats that require immediate action are flagged, while lower-priority risks are monitored.
4. Automated Response
If the system detects a critical threat, it can trigger an automated response, such as blocking malicious traffic or isolating a compromised system. This ensures that action is taken even before human analysts are notified.
5. Continuous Learning
AI systems continuously learn from each threat they encounter. This helps improve detection capabilities and reduces false positives over time.
Things to Keep in Mind While Implementing AI in SOC
Implementing AI in a SOC can greatly enhance security operations, but it requires careful planning to be effective. Here are some important considerations:
1. Data Quality
AI systems need access to high-quality data to function effectively. To improve threat detection accuracy, ensure that your data collection processes are thorough and consistent.
2. Integration with Existing Systems
AI-driven SOCs should integrate seamlessly with your current IT infrastructure. Ensure your SIEM, threat intelligence platforms, and other tools work well with AI technologies.
3. Trained Personnel
While AI can automate many tasks, human expertise is still essential for managing complex incidents. Ensure your security expertise team is trained to work alongside AI systems, interpreting data and making high-level decisions when necessary.
4. Cost Considerations
AI systems can be expensive to implement, especially for smaller organisations. It’s essential to weigh the costs against the potential benefits and ensure that the solution meets your security needs.
5. Ongoing Maintenance
AI systems require regular updates and maintenance to function correctly. You should ensure that your IT team is well-prepared to handle this ongoing responsibility.
Why AI native SOC Architecture is the Future of Cybersecurity
The volume and complexity of security attacks are increasing at an unprecedented rate. Organisations can no longer depend solely on the human brain to address these challenges.
AI-powered SOC architecture provides a solution that is fast, scalable, and continuously improving.
With its ability to predict, detect, and respond to threats, AI is transforming the management of security operations, making organisations more resilient in an ever-changing threat landscape.
How can Aztech help?
Aztech’s experienced security professionals utilise an AI-driven SOC with Microsoft Sentinel to help protect your digital assets.
Aztech empower your security teams to detect, investigate, and respond effectively, which also helps lower your total cost of ownership.
Aztech offer a unified security operations platform that combines the capabilities of Extended Detection and Response (XDR) and Security Information and Event Management (SIEM).
Microsoft Sentinel provides both SIEM and Security Orchestration, Automation, and Response (SOAR) functionalities in a single solution.
Summary
AI SOC architecture represents the next evolution in cybersecurity. It combines the best of human expertise and machine intelligence to protect organisations more effectively.
As cyber threats continue to advance, AI SOCs will become an essential component of any robust security strategy. Whether you're looking to improve threat detection, reduce costs, or streamline your security operations, an AI-driven SOC is the solution.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)






.png?width=536&name=Blog%20Hero%20Banners%20(9).png)

