As cyber security professionals, we know the importance of staying vigilant and protecting against malicious actors to keep our online information safe.
However, with the rising popularity of social engineering techniques in hacking, it's important to have a clear understanding of what this type of attack is and how we can protect ourselves against it.
In this blog post, we'll explore an introduction to social engineering attacks within the context of hacking as well as some useful tips for defending against them. Read on for more information!
What is social engineering in hacking?
Social engineering is a hacking technique that involves manipulating people to gain unauthorised access to sensitive information or systems.
In this method, a hacker exploits the natural human tendency to trust others and uses various tactics to deceive the victim into divulging confidential information.
These tactics could range from posing as a trusted authority figure through a fake email or phone call, to creating a fake login page that mimics a legitimate website.
Social engineering attacks can have devastating consequences, leading to financial loss, identity theft, and even compromising the security of an entire organisation.
It is important to remain vigilant and educate yourself on common social engineering tactics to protect yourself and your information.
Social Engineering, in the context of information security is,
the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes
There are a variety of Social Engineering strategies cyber criminals use, which you can read.
Best Social Engineering Attack Example
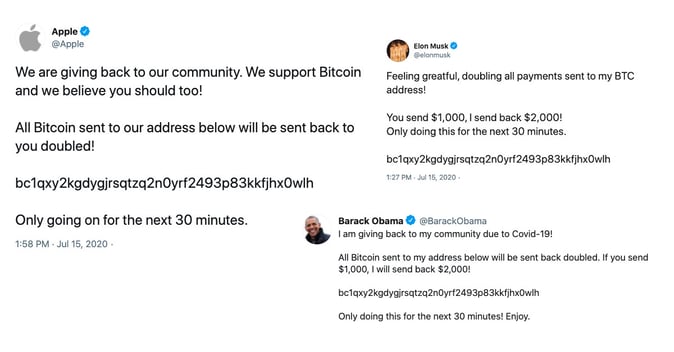
On Wednesday 15th July 2020, Twitter became a victim of a cyberattack. The hack compromised 130 accounts, including Barack Obama, Elon Musk and Bill Gates to name a few. These compromised accounts posted tweets urging their followers to send them money in Bitcoin, stating the transaction would be doubled.
As the investigation is still underway, new information is being released periodically. The latest update revealed usernames were attempted to be sold, and accounts had their email addresses, phone numbers, and direct messages accessed on certain accounts.
How did this happened?
Twitter released a statement on Saturday 18th July that explained their employees had succumbed to a Social Engineering attack. The attackers had successfully manipulated a small number of their employees into handing over their credentials.
These credentials were used to access Twitter's internal systems, which included getting past two-factor authentication.
Allegedly, the hacker managed to find admin credentials within their Slack channels and used this to further hack into Twitter's systems.
Out of the 130 accounts that were targeted, 45 accounts had passwords reset and tweets compiled asking for Bitcoin payments.
Why should you care about this?
Twitter is a large business and one of the top social media platforms, so you would expect it to have excellent security protocols in place to help protect their data from cyber attacks. However, as we saw last week, if your employees succumb to a social engineering attack and give away their credentials, it doesn't matter how effective your security is - your business can still be hacked and your data will be at risk.
Whether your business is large or small, your employees should be a key part in your security strategy. Cybercriminals know that your employees are the easiest way for them to access your data, thus making them your weakest link. This is why they send highly-targeted emails that could trick even the savviest user into handing over their credentials.
How to prevent social engineering
Here are seven effective ways through which you can prevent social engineering attacks:
1. Be Aware of Potential Scams
The first step to preventing social engineering is to be aware of potential scams. Social engineers often rely on deception and manipulation to gain access to sensitive information or resources.
It is important to recognise the signs of a potential scam, such as unsolicited emails or phone calls from unknown numbers.
If you receive any suspicious requests, it is best to be cautious and verify the source before providing any information.
2. Be Wary of Unsolicited Requests
Social engineers often target individuals by sending unsolicited requests for personal information or money. It is important to be wary of these types of requests, even if they appear to come from a legitimate source.
Before responding, take the time to verify the source and make sure that the request is legitimate.
3. Verify Sources Before Providing Information
When dealing with any type of request for personal information or money, it is essential to verify the source before providing any information or funds.
If possible, try to contact the organisation directly to confirm their identity and authenticity before providing any sensitive data.
4. Use Strong Passwords & Two-Factor Authentication
Using strong passwords and two-factor authentication can help protect your accounts from social engineering attacks.
Strong passwords should include a combination of letters, numbers, and special characters, while two-factor authentication requires an additional step (such as entering a code sent via text message) to access an account.
5. Educate Yourself & Others on Social Engineering Tactics
Educating yourself and others on social engineering tactics can help prevent future attacks by making people more aware of potential scams and how they work.
There are many online resources available that provide detailed information about social engineering tactics and how they can be prevented or avoided altogether.
6. Report Suspicious Activity Immediately
If you suspect that you have been targeted by a social engineer, it is important to report the activity immediately so that it can be investigated further by law enforcement or other authorities who specialise in cyber security matters.
Reporting suspicious activity promptly can help prevent future social engineering attacks from occurring and protect other individuals from becoming victims as well.
7. Utilise Cyber Security Software & Services
Finally, utilising cyber security software and services can also help protect against social engineering attacks by monitoring online activity for suspicious behaviour or malicious activity that may indicate an attack is underway or being planned out by a potential attacker.
How can you stop social engineering fraud?
Cybercriminals' tactics change frequently, which is why you should provide your users with regular training and updates on the latest security threats.
- Make your users aware of how they can help protect your organisation, especially as this can help them protect their own data in their general day to day lives.
- If your users are properly educated and trained on the threats of cyber attacks, including the warning signs of social engineering, they can help keep your data protected.
- User awareness training is designed to make your users think twice about an email, phone call, or even the dangers of using a USB stick they find - this training is not just for new users either, it can benefit users at all levels and any department.
How AZTech can help
Our User Awareness Training helps educate your users on cyber threats, suspicious activity, and how to stay safe online.
With 90% of security breaches occurring due to human error, user awareness training is key in keeping your organisation protected against cybercrime.
Furthermore, we can help you put together a backup and recovery plan, as sometimes it is not a matter of, "if a cyberattack will happen", but rather when - if your organisation is not prepared for an attack, you could lose all your data, especially if it is encrypted and held for ransom.
Cybercriminals do not care if your organisation is large or small, if they know they can access your data and benefit financially from it, they will.
Protect your business today - get in touch with us to find out more.
Related Articles:

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)

-2.png?width=1366&height=768&name=Blog%20Hero%20Banners%20(4)-2.png)
-2.png?width=1366&height=768&name=Blog%20Hero%20Banners%20(5)-2.png)