Everything you should know about Shadow IT
"Shadow IT" is an umbrella term used to describe any type of IT system, software, hardware, application, or service that isn't known or managed by your IT department.
Cisco's research has shown that 80% of end users use software not cleared by IT, 83% of IT staff admit to using unsanctioned software or services, and only 8% of all enterprises know the scope of Shadow IT within their organisation.
In this blog post, we'll discuss what shadow IT is, why it's important, risk and challenges, benefits and some best examples for mitigating any potential risks associated with shadow IT.
So, keep reading if you want to learn more about this complex issue facing every modern business today!
What is Shadow IT?
Definition of Shadow IT
Shadow IT refers to the usage of unauthorised software, applications, or devices by employees within a company without the knowledge or approval of the IT department.
Shadow IT refers to any IT system or technology solution that is implemented within an organisation, without the approval or knowledge of the IT department. This covert practice raises several concerns regarding data security, operational efficiency, and overall IT governance.
As you can imagine, this can lead to a whole host of potential issues, including security risks, data loss, and compliance violations.
While shadow IT may initially seem like a smart solution for departments or individuals looking to streamline processes or increase efficiency, it's important for organisations to recognise the potential dangers and take steps to manage and regulate these systems.
In short, shadow IT can be a double-edged sword – useful in some cases, but ultimately a risk that needs to be evaluated and mitigated.
Unveiling the Growing Problem of Shadow IT
Nowadays, businesses are faced with an escalating issue known as shadow IT. In this article, we will explore why shadow IT has become a significant concern and delve into its implications for organisations.
Reasons for Growing Problems of Shadow IT
1. Flexibility and Convenience
One reason why shadow IT has gained traction is the desire for more flexibility and convenience.
Employees often turn to unauthorised tools or software to streamline their workflows, enhance collaboration, and meet their unique requirements.
2. Lack of Awareness
Another contributing factor is the lack of awareness among employees about the risks associated with shadow IT.
Many may not fully comprehend the potential pitfalls, such as data breaches, compliance violations, or compatibility issues.
3. Slow IT Processes
Some employees resort to shadow IT due to frustration with slow IT processes. When faced with extensive waiting times or bureaucratic procedures, individuals may take matters into their own hands, seeking immediate solutions to their technological needs.
Impact of Shadow IT
The proliferation of shadow IT can have far-reaching consequences for organisations.
It fosters a fragmented IT landscape, making it challenging to maintain control, ensure compliance, and safeguard sensitive data.
Moreover, shadow IT can hinder collaboration and standardisation efforts, exacerbating operational inefficiencies.
Shadow IT Risks and Challenges
What are the risks of shadow IT?
1. Security Vulnerabilities
Shadow IT can expose organisations to increased security risks, such as data breaches, malware infections, or unauthorized access to sensitive information.
Without proper monitoring, these unapproved tools may lack the necessary security measures.
2. Compliance Concerns
By bypassing IT department regulations and standards, using unauthorised software can result in non-compliance with industry regulations, such as GDPR or HIPAA.
This can lead to severe legal and financial repercussions for the organisation.
3. Data Loss or Leakage
When employees handle sensitive data using unapproved tools, data loss or leakage becomes a significant concern.
Unsecured file-sharing platforms or unsanctioned communication applications can put confidential information at risk.
What are the challenges in Managing Shadow IT?
1. Lack of Visibility
One of the biggest challenges in tackling Shadow IT is the lack of visibility into what unauthorised tools employees are using.
Without proper monitoring and oversight, it becomes difficult for organisations to assess and mitigate potential risks.
2. Employee Productivity and Collaboration
While employees may turn to Shadow IT to enhance their productivity or collaboration efforts, the use of unapproved tools can create a fragmented IT environment.
This can lead to data silos, inefficient workflows, and compatibility issues.
3. IT Department Collaboration
Effective management of Shadow IT requires close collaboration between the IT department and other business units.
However, without clear communication and understanding, bridging this gap can be a challenge.
What are the benefits of shadow IT?
Shadow IT, often seen as a challenge, can actually bring several advantages to organisations. Though it refers to the use of unauthorised or unmanaged software and services within a company, it can foster innovation and productivity in unexpected ways.
The Benefits of Shadow IT are:
1. Agility and Flexibility
Shadow IT allows employees to quickly adopt new tools and technologies that meet their specific needs, without going through the lengthy IT approval process.
This agility enables teams to be more responsive to changing business requirements.
2. Innovation and Experimentation
Unconstrained by formal processes, employees can explore new software and solutions that might not have been considered by the IT department.
This freedom to experiment encourages innovation and can lead to breakthrough ideas.
3. Customisation and Personalisation
Shadow IT empowers users to choose software that best fits their individual workflows and preferences.
This customisation and personalisation can enhance productivity and user satisfaction.
4. Cost Savings
By leveraging free or low-cost cloud services, employees can meet their needs without incurring additional expenses for the organisation.
This can result in significant cost savings, especially for smaller business units.
5. Rapid Problem Resolution
Shadow IT often brings about a community of employees who are knowledgeable about a wide range of applications.
When issues arise, these individuals can share insights and collaborate to find quick solutions, reducing downtime.
It is important to note that while Shadow IT can offer these advantages, it also poses security and compliance risks.
Therefore, organisations should implement proper governance and establish clear communication channels to maximise the benefits while mitigating the potential drawbacks.
What are the examples of Shadow IT?
Here are some of the Shadow IT examples:
1. Personal Cloud Storage
Employees may use personal cloud storage services such as Dropbox or Google Drive to store and share company files, which can pose security risks.
2. Messaging Apps
Employees might utilise messaging apps like WhatsApp or Slack for work-related communication, bypassing official channels and potentially compromising data privacy.
3. Project Management Tools
Some teams may opt for project management tools like Trello or Asana without IT approval, leading to data fragmentation and potential integration issues.
4. Collaboration Tools
Employees may adopt collaboration tools like Microsoft Teams or Zoom for remote work collaboration, even if they are not officially supported by IT, causing compatibility and security challenges.
5. Bring Your Own Device (BYOD)
Employees using personal devices to access company resources without appropriate security measures can result in data breaches and compliance issues.
Understanding examples of Shadow IT helps organisations proactively mitigate associated risks and develop appropriate policies and procedures.
By addressing the underlying needs driving the usage of Shadow IT, companies can foster a culture of innovation while safeguarding data and maintaining compliance.

How can you manage Shadow IT?
The cloud helps increase flexibility for your users and IT, but it introduces new challenges and complexities for your business.
Your users are now incredibly self-sufficient, they have an understanding of computer technologies, and know which apps and software can help their job roles be more efficient.
Modern businesses now work across multiple devices, from desktops and laptops to handheld smart devices, but do you know how many cloud apps your users are using?
The average answer companies guess is typically 30 - 40 apps, but in actuality, it can be over 1000 - so, how can you discover and manage this to help prevent risk to business?
It's no longer enough to rely on your firewalls as your teams can access your data outside of your corporate network, you need to utilise tools such as Cloud App Security.
You can discover and identify Shadow IT using Cloud Discovery within Cloud App Security - this finds the apps your users are using and allows you to explore the risks of the apps and configure policies so any new apps will be analysed for risk to business.
Cloud App Security assists with the process of managing app use in your business, once you've identified the behaviours and patterns in your organisation, you'll be able to create custom app tags to classify each app according to business status and more - these tags can be used for specific monitoring such as traffic to high-risk apps.
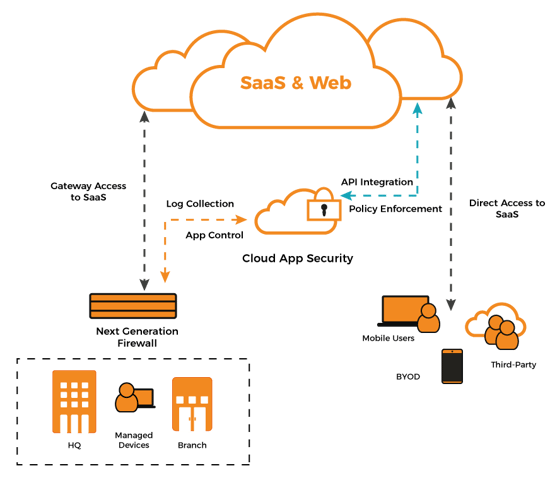
Shadow IT Policy
In simple words, Shadow IT Policy refers to the set of guidelines and rules established by organisations to address the use of unauthorised or unapproved technology solutions within their network.
By implementing this policy, businesses aim to mitigate security risks, ensure compliance with regulations, and maintain control over their IT infrastructure.
It serves as a vital tool for educating employees about cyber security and the potential dangers of using unregulated software or hardware, and provides a framework for managing and monitoring technology usage across the organisation.
Shadow IT Policy Example
Shadow IT policies encompass a wide range of examples. Some common ones include:
- The use of unauthorised cloud services
- Unapproved software installations
- The utilisation of personal devices for work purposes
These policies are designed to address the potential risks and challenges associated with Shadow IT and ensure a secure and compliant IT environment.
Shadow IT Policy Template
Here are the elements of a Shadow IT Policy Template:
1. Definition
Begin by clarifying what Shadow IT is and why it matters. Explain that it refers to the use of technology or software by employees without the knowledge or approval of the organisation's IT department.
2. Risks and Consequences
Discuss the potential risks and consequences associated with Shadow IT. Highlight how it can compromise data security, hinder collaboration, and lead to compliance issues.
3. Policy Guidelines
Provide clear guidelines and expectations regarding the use of technology within the organisation. Emphasise the importance of employees consulting with the IT department before adopting new tools or software.
4. IT Support and Training
Offer information on the support and training resources available to employees. Encourage them to seek assistance from the IT department whenever they have technology-related needs or questions.
5. Reporting Mechanism
Establish a reporting mechanism for employees to report any suspected instances of Shadow IT. Assure them that their concerns will be taken seriously and addressed promptly.
By implementing a comprehensive Shadow IT policy, organisations can effectively manage technology usage while maintaining data security and productivity.
Want to discuss how you can take back control? Get in touch by calling us on 03300 949 420, or use the button below to request a consultation with one of our experts today.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)






-1.png?width=536&name=Blog%20Hero%20Banners%20(5)-1.png)
