Every day, the complexity of cyber attacks and the cybercriminals behind them advance - if you're a small or medium-sized business (SME) utilising one of Microsoft's 365 environment plans, you are still at risk of a cyber attack.
This article aims to provide information that will help you prevent your Microsoft 365 environment from being hacked, highlighting the required precautions necessary to help strengthen your security level and awareness.
Over recent years, and exponentially over the last year, businesses have transitioned to cloud computing to enable remote working or work from home flexibility, and benefit from such services.
However, with this comes added risks from cybercrime or employee ignorance. With threats ever-evolving, many organisations struggle to maintain security over their environments.
This below video explains about the top 5 security settings you need to switch on now for the best practices for business security with Microsoft 365.
We are looking to educate IT managers and business owners on best practices for business security with Microsoft 365 Security and protect their data and users.
17 Best Practices for Business Security with Microsoft 365
Here are 17 steps you can take to secure your business with Microsoft 365:
1. Enable Multi-Factor Authentication (MFA)
One of the best practices for Microsoft 365 security is Multifactor Authentication. It is a verification method that's used to reduce risk when you sign in to your Microsoft 365 account.
When you wish to access your online accounts, you move through a process of "authentication" - in essence, you are providing evidence to prove who you say you are.
This is most important when signing into your account for the first time on a new device or application as you need more than just a username and password.
With MFA enabled, you are required to supply additional proof to prevent unauthorised access, which is called "factor" - this adds an additional layer of security to your account to keep your data protected.
MFA should be adopted as Basic Security Practices in all organisations.
Different factors needed to authenticate with MFA:
• Something you know, like a password or a memorised PIN• Something you have, like a trusted device (smartphone, or a secure USB key)
• Something you are, like biometrics, fingerprints, or facial recognition
2. Stop Auto Forwarding for Email
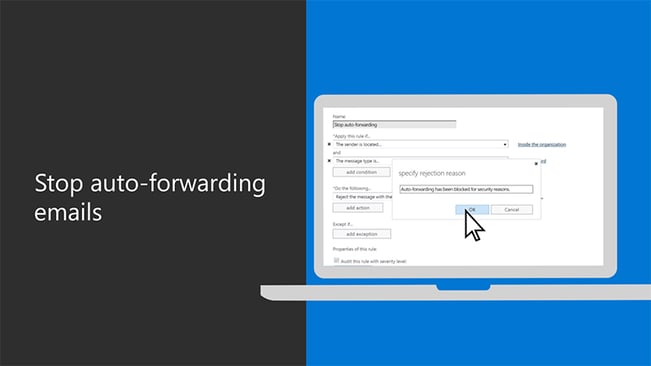
Another best practices for business security with Microsoft 365 is to disable auto forwarding emails.
As part of any good Security Awareness Training - educating the user of the risks of their own habits is key to reducing security breaches.
Adopting a clear communication strategy to explain why automatic email forwarding is a bad idea and how it is still the most common way sensitive data leaves an organisation.
Automatic email forwarding is common amongst employees where they have corporate email accounts forward all email to personal accounts.
Risks occur when data remains in personal, less secure, accounts or in the event of a user no longer working for the company.
Disabling automatic email forwarding to the outside of the organisation is good practice to ensure advance email protection.
3. Use Strong Passwords or a Password Manager

Use of a password manager is one of the best practices for business security with Microsoft 365.
Traditionally, it was considered best to memorise passwords; this led to, and continues to be, one of the major culprits to security. The reuse of the same, or derivatives, of a password.
But password managers generate long, unique, complex passwords, and store them securely in their database.
Password managers typically allow you to enter login details across browsers and devices with a click of a button - this is either achieved by either in-app links or browser extensions.
Password managers help prevent phishing attacks as they often have a data breach feature that lets you know if a website or password has been corrupted.
4. Use Office Message Encryption

Message Encryption allows you to send and receive sensitive information across an email.
Microsoft Office Email encryption is best practice for business security as it ensures that only the intended recipients can view the message content.
With the advanced features, encrypted emails can only be accessed through a Microsoft 365 web portal, and more control can enhance protection such as message revocation and expiration, sensitive information detection to name but a few.
5. Configure Conditional Access
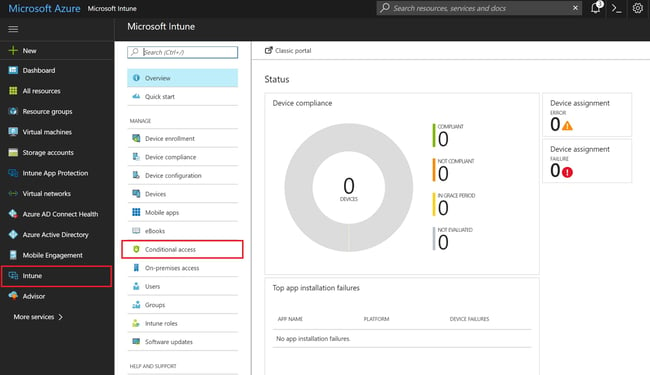
One of the best practices for business security with Microsoft 365 is to set up conditional access as it automate control over accessing your cloud applications.
Cloud computing services have the benefit of accessing the apps and their data from anywhere, but the downside is that cybercriminals can also do the same.
Conditional access allows you to restrict access through Device management, location, IP addresses, users/groups, and applications.
6. Review and use Microsoft Secure Score
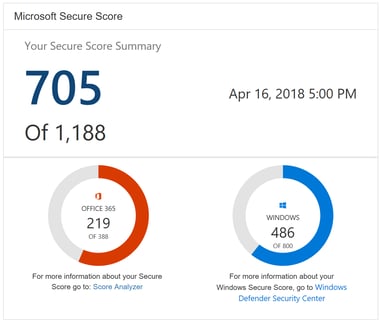
Microsoft Secure Score measures your organisation's security posture. The higher the number of the score, the greater the number of actions taken.
Each recommended action can protect your Microsoft 365 environment from threats.
This can be easily monitored from a centralised dashboard in the security centre where steps to improve security can be easily reviewed.
7. Run a Simulated Phishing attack and train your users
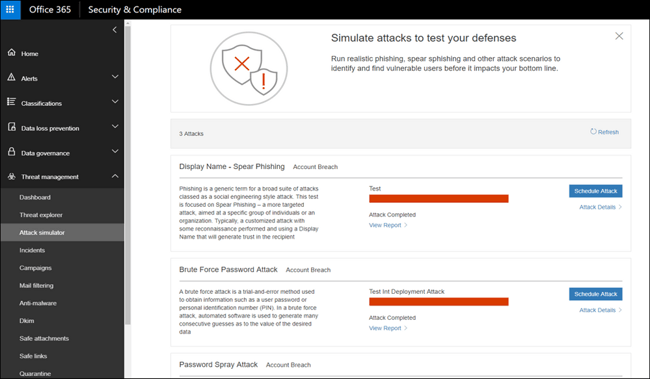
A simulated phishing attack is a quick penetration test that will establish whether or not your organisation is vulnerable to such a threat.
Employees are typically the weakest link in an organisations security, so this test can quickly assess the situation of your cybersecurity posture.
You can run a realistic simulated attack from inside Microsoft Defender for Office 365.
These feign threats are preparation for the real attack and allow identification of user vulnerabilities.
8. Setup Spoofing protection
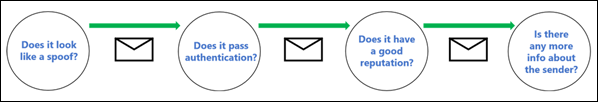
Another best practices for business security with Microsoft 365 is anti-spoofing protection. This can help mitigate phishing attacks from spoofed (fake) senders and domains.
Spoofed messages are those that appear to originate from someone when, in fact, they originate from another source.
When the Exchange Online Protection (EOP) is enabled, spoofed messages are examined for forgery attempts in the 'From' header in the message body.
This procedure identifies the message sender with high confidence and determines if the message is spoofed.
9. Protect against malicious attachments and files with Safe Attachments
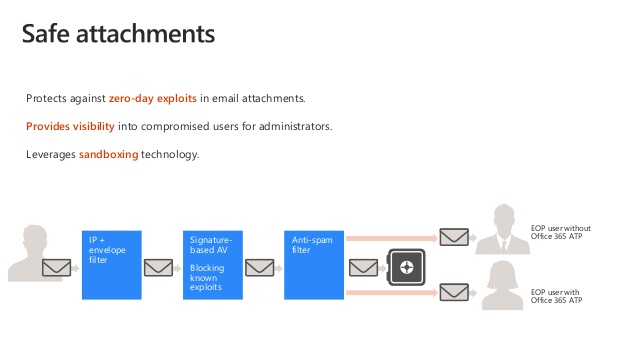
Microsoft Defender for Office 365 provides an additional layer of protection against malicious email attachments.
Files that have already been scanned by anti-malware protection in Exchange Online Protection (EOP) are checked in a virtual environment before being delivered to the recipient. This process is commonly known as a detonation.
Safe Attachments operates by "use of policies" as there are none by default - you are required to create one or more to enable the added cyber security.
10. Protect your email from phishing attacks

Ensure that you set Microsoft 365 to update automatically. The latest patch will protect you against the latest security threats.
Another action you can take is regularly backing up your data. Save this backup in a place not connected to your network; this could be a trusted device such as an external hard drive or cloud storage.
This is a must for desktop computers, laptops and mobile phones.
11. Configure OneDrive Known Folder Protection
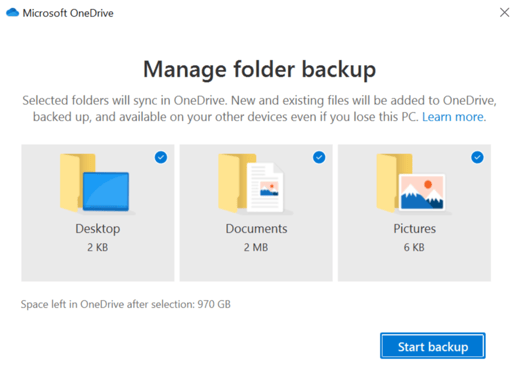
Another best practice for business security with Microsoft 365 is OneDrive Known Folder Move. This allows for easy migration of important Windows folders to a users personal cloud storage.
The move of private data from the profile to OneDrive ensures that users do not lose important data from their computers and that all content is automatically synced across different devices.
12. Configure Data Loss Prevention (DLP) Policies
![]()
Once you apply Data Loss Prevention (DLP) Policies with your Microsoft 365 Security & Compliance Centre you will be in a position to identify, monitor, and automatically protect your sensitive information across your Office 365 environment.
A DLP can find sensitive data across applications (such as Exchange Online, SharePoint Online, OneDrive etc.)
This allows you to pinpoint any document or email message that contains financial data or Personally Identifiable Information (PII), and then automatically block access to that email or document.
13. Configure Mobile Device Management (MDM)
.png?width=650&height=394&name=Configure%20Mobile%20Device%20Management%20(MDM).png)
With more employees utilising personal devices for work, new challenges have arisen for your company's security culture.
Microsoft's Enterprise Mobility Suite is a simplified service to manage users and devices that wish to access company files, which is why it's crucial to establish data policies that encompass the handling of business data on personal devices.
This would also include encryption, passwords, and maintaining a clear distinction between personal/work information.
Security teams should adopt these best practices for business security that would resolve issues such as, lost devices or corporate resources being removed from personal devices of employees that no longer need access to them.
14. Use dedicated admin and role-based accounts
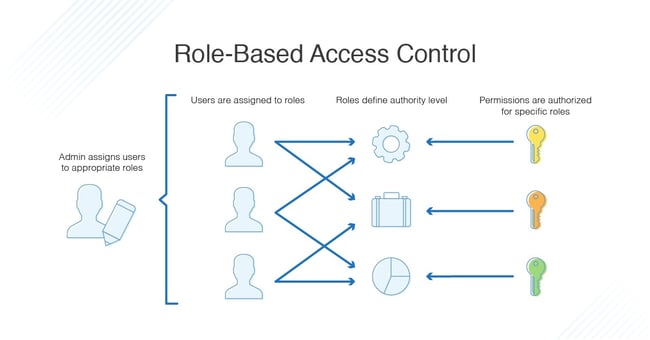 Dedicated admin roles can be assigned specific permissions that work alongside business functions to complete relevant tasks.
Dedicated admin roles can be assigned specific permissions that work alongside business functions to complete relevant tasks.
Microsoft 365 admin centre lets you manage and customise the permissions and roles to work for your business.
15. Setup logging, auditing, and reporting
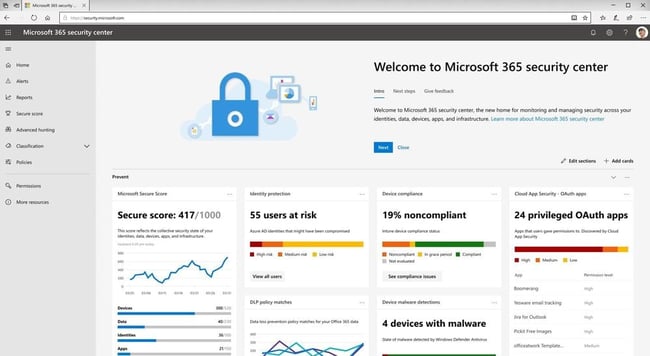
Microsoft's Security and Compliance Centre can search and access audit logs to view user activity.
Such activities can include whether a user viewed a particular document or removed a document from their inbox.
Additional features allow for audit reports, such as the number of active and inactive users in the Microsoft 365 environment, and calculating the amount of mail within the organisation.
Each report can be applicable to the last 7, 30, 90 or 180 days.
16. Consider third-party advanced email protection
.jpg?width=650&height=271&name=Consider%20third-party%20advanced%20email%20protection%20(such%20as%20Mimecast).jpg)
The use of third-party tools, such as Mimecast, is one of the best practices for business security as to add layered email security.
Mimecast can create advanced filtering, which is great for blocking spam, malware, viruses, filter connection, and keep your mailboxes safe.
Integrating services such as Mimecast will easily reduce risk and complexity when it comes to minimising disruption.
The employment of highly sophisticated detection engines and the latest threat intel ensure email security defences are up to date and kept up and running.
17. Configure a third-party backup solution for Microsoft 365
When looking for a 3rd party backup solution, such as Druva Office 365 Backup, you will want a service that can handle scenarios such as data loss or ransomware attacks.
In such an event, a third-party backup will provide the best data retention and allow you to quickly obtain your data. Backup management can be performed with just a few clicks saving you time and safeguards business projects.
Microsoft 365 Security Checklist
The Microsoft 365 Security Checklist is a comprehensive guide that ensures your digital environment is protected.
With easy-to-follow steps, this checklist helps you enhance your security measures, safeguard your data, and protect against potential threats.
By implementing the recommendations outlined in this checklist, you can bolster your defence, minimise vulnerabilities, and ensure the utmost security for your organization's digital assets.
Download the Microsoft 365 security checklist
If you haven't reviewed or need our assistance securing your Microsoft 365 Environment, then get in touch for your free audit, and we will establish a report and provide recommendations to help secure Microsoft 365 and protect your data.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)

-2.png?width=1366&height=768&name=Blog%20Hero%20Banners%20(4)-2.png)
-2.png?width=1366&height=768&name=Blog%20Hero%20Banners%20(5)-2.png)

.png?width=651&height=293&name=Enable%20Multi-Factor%20Authentication%20(MFA).png)



