Editors Note: This blog post is detailed research on the evolving cyber security trends in business sectors and was updated in November 2024.
The main factors driving the latest cybersecurity trends for 2025 are Generative AI (Gen-AI), state-sponsored cyber warfare, zero-trust architecture, boardroom communication gap, advanced phishing techniques (QR phishing & BEC), 5G, and IoT security, and cybersecurity skills shortage.
As we step into the beginning of 2025, the importance of cybersecurity has never been more evident. With each passing year, new threats emerge, and existing ones evolve, challenging organisations to stay one step ahead in the ongoing battle against cybersecurity threats.
In this comprehensive blog post, we have researched the latest trends in cybersecurity shaping the landscape from 2024 to 2025, offering insights and strategies to help businesses navigate emerging cyber threats.
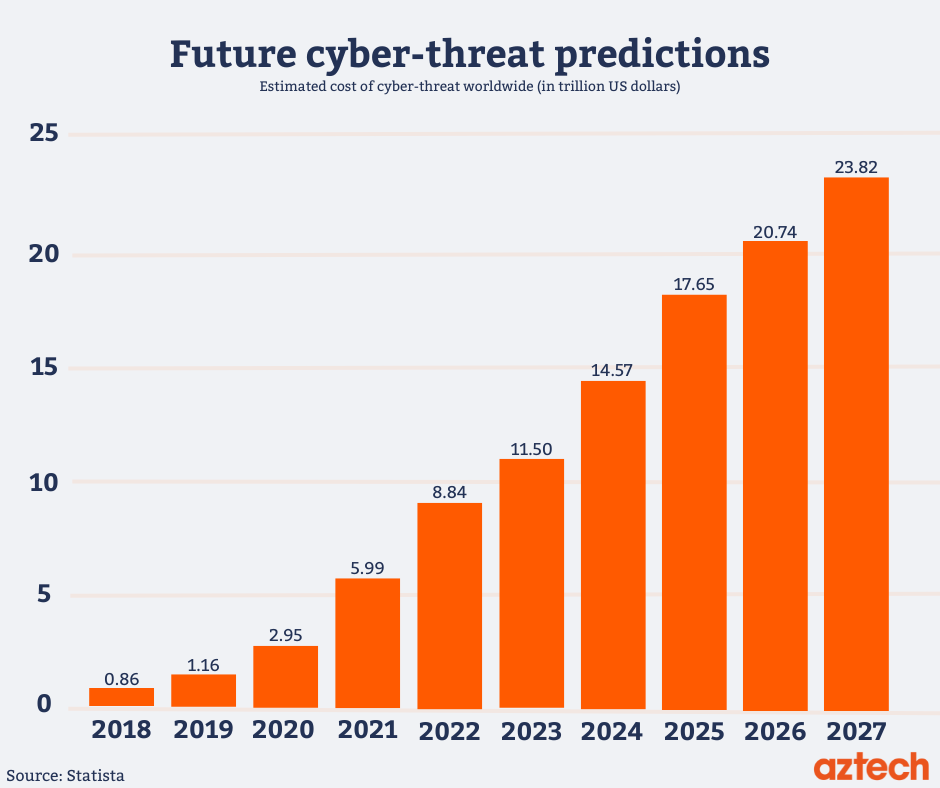
What are the top cybersecurity trends of 2025?
Here is the list of latest cybersecurity trends to watch out for in 2025 and beyond:
Trend 1. Use of Generative Artificial Intelligence (Gen-AI)
Generative Artificial Intelligence (Gen-AI) is revolutionising the cybersecurity industry in 2025 by enabling security leaders to predict cyber threats with unprecedented accuracy.
Gen-AI is the talk of the town right now with applications such as OpenAI’s ChatGPT, Google’s Gemini and Microsoft’s Copilot are just the beginning of its impact on the field.
By leveraging Large Language Models (LLMs) and machine learning algorithms, Gen-AI can build automated security systems like natural language processing (NLPs), threat intelligence, face detection and automated threat detection.
The UK AI market is valued at over £16.9 billion and is projected to reach £803.7 billion by 2035. Over the past decade, UK AI companies have surged by 688%. Additionally, 68% of large companies, 33% of medium-sized companies, and 15% of small companies have adopted at least one AI technology.
Government data shows the most commonly adopted AI solutions in the UK focus on:
-
data management and analysis (9%)
-
natural language processing and generation (8%)
-
machine learning (7%)
-
AI hardware (5%)
-
computer vision and image processing and generation (5%).
GCHQ’s National Cyber Security Centre warns that AI will significantly increase global ransomware threats, with a new report indicating that artificial intelligence is likely to elevate both the frequency and severity of cyber threats over the next two years.
NCSC CEO Lindy Cameron stated:
“We must harness AI technology for its potential while managing its risks, especially concerning evolving cyber threats. The use of AI in cyber attacks enhances existing threats like ransomware but does not fundamentally change the risk landscape in the near term.
As the NCSC ensures AI systems are secure by design, we encourage organisations and individuals to follow our ransomware and cyber security best practices to strengthen defences against cyber attacks.”
The National Crime Agency (NCA) reports that cyber criminals are developing criminal Generative AI (GenAI) and offering it as a paid service. However, the National Cyber Security Centre (NCSC) notes that the effectiveness of these GenAI models will be limited by the quality and quantity of their training data.
Trend 2. Cybersecurity Risks in Remote Work
After the pandemic, more and more companies are shifting towards remote work. This has introduced new cybersecurity challenges, as organisations struggle with securing distributed networks and endpoints.
Additionally, with social engineering attacks like SIM swapping targeting remote employees to vulnerabilities in remote access tools, the security risks associated with remote work are numerous.
In 2025, businesses should prioritise investments in remote security solutions and employee training programmes to mitigate these risks effectively.
As per the UK government’s cyber security breach survey 2024, 68% of UK businesses have remote or mobile working listed in their cyber security policies. Also, 44% of UK employees work from home at least some of the time (hybrid or full-time, remote workers).
Trend 3. Continuous Threat Exposure Management (CTEM) Programmes
Traditional approaches to cybersecurity often focus on point-in-time assessments, leaving organisations vulnerable to emerging and evolving threats.
Continuous Threat Exposure Management (CTEM) programmes offer a proactive alternative, providing real-time visibility into security risks and vulnerabilities across the entire digital ecosystem.
By implementing Continuous Threat Exposure Management (CTEM) initiatives, organisations can consistently assess the accessibility, exposure, and exploitability of both digital and physical assets.
According to Gartner, by 2026, organisations that prioritise their security investments based on a CTEM program are expected to achieve a two-thirds reduction in security breaches.
A recent market research report from Global Market Estimates indicates that the global CTEM market is projected to grow at a compound annual growth rate (CAGR) of 10.1% from 2024 to 2029.
Trend 4. Rise of State-Sponsored Cyber Warfare
The geopolitical landscape is increasingly shaping the cybersecurity threat landscape, with nation-states engaging in cyber warfare as a means of espionage, sabotage, and geopolitical influence.
In the years ahead, we expect to see a proliferation of state-sponsored cyberattacks targeting critical infrastructure, government agencies, and multinational corporations.
To defend against these threats, organisations must adopt robust cybersecurity measures and collaborate with government agencies and international partners.
In the United Kingdom, NHSC and UK government bodies are helping organisations with cyber security awareness training and programs.
Trend 5. Reimagining Trust: A Less Than Zero Trust Approach
The Zero Trust security model operates on the principle that no user or device is inherently trusted, a concept that has become increasingly popular in recent years.
However, as cyber threats become more sophisticated, security leaders are reimagining trust in the digital era with a "Less Than Zero Trust" approach. This paradigm shift involves continuously verifying and validating user identities, devices, and applications, regardless of their location or access privileges.
Zero Trust Network Architecture (ZTNA) is now widely accepted. In just two years, more organisations have adopted this security approach. Currently, 61% of organisations have a Zero Trust initiative in place, and another 35% plan to set one up soon.
Key findings from the 2024 State of Zero Trust & Encryption Study include:
- Two-thirds of organisations say that worries about cyber risks are their main reason for adopting a zero-trust strategy. In the UK, this is even more evident, with 50% of organisations citing cyber breach risks and 29% mentioning a growing attack surface.
- Although 59% of organisations report strong support from senior leaders for Zero Trust, they still struggle with a lack of skills and budget. This shows a gap between support and the resources needed for successful implementation.
- Zero Trust adoption is on the rise, yet is lagging in Western countries. While 61% of organisations have started their Zero Trust journey, only 48% of U.S. organisations have begun, indicating a struggle to implement these proactive security measures and exposing them to cyber threats.
- Relying solely on good cyber hygiene is insufficient. A recent survey revealed that 46% of respondents identified hackers exposing sensitive data as their top concern, followed by system malfunctions and unmanaged certificates. For the first time in eight years, employee mistakes did not rank as a major threat.
Additionally, organisations face challenges in credential management due to a lack of skilled personnel (50%), unclear ownership (47%), and inadequate staffing (46%).
Trend 6. Improving Boardroom Communication Gap
Effective communication between cybersecurity professionals and corporate boards is essential for ensuring adequate investment in cybersecurity initiatives and alignment with business objectives.
In the coming years, organisations should bridge the communication gap between technical experts and board members, translating complex cybersecurity risks into business-centric language and metrics that resonate with decision-makers.
Gartner states that Original Device Manufacturers (ODMs) are key for developing an effective cybersecurity investment strategy. They help define clear protection levels that are easy for non-IT executives to understand. This approach creates a reliable way to express risk tolerance, which supports direct investment to improve protection levels.
Trend 7. Advanced Phishing Techniques
Phishing remains one of the most prevalent and effective cyber-attack vectors, with threat actors constantly evolving their tactics to evade detection and deceive unsuspecting victims.
From spear-phishing to business email compromise (BEC), cybercriminals are employing increasingly sophisticated techniques to infiltrate organisations and steal sensitive information.
To combat this threat, organisations should prioritise employee awareness training and deploy advanced email security solutions.
Advanced phishing techniques in 2024 are quishing or QR code phishing.
Egress Email Security Risk Report 2024 identifies the most prevalent phishing attack types: malicious URLs, compromised trusted third-party accounts, and malware or ransomware.
The findings are alarming.
94% of organisations have confronted phishing attacks, with 96% experiencing negative repercussions. In 74% of cases, employees involved faced disciplinary action, dismissal, or chose to leave.
Account takeover attacks impacted 58% of organisations, with 79% of these incidents originating from phishing emails and 83% successfully bypassing multi-factor authentication (MFA).
Cybersecurity leaders are justifiably concerned, with 61% expressing anxiety over the threat posed by chatbots in phishing schemes.
Furthermore, 91% have serious reservations about their Secure Email Gateways (SEGs), and 90% are uneasy about their static Data Loss Prevention (DLP) rules.
Trend 8. Growing Threat of Cyber Attacks on Mobile Devices

With the proliferation of mobile devices in the workplace, cybercriminals are increasingly targeting smartphones and tablets as vectors for cyberattacks.
From mobile malware to malicious apps, the threat landscape for mobile devices is evolving rapidly, posing significant risks to organisations' data security and privacy.
To mitigate these risks, organisations should implement robust mobile security policies and leverage mobile device management (MDM) solutions to secure corporate-owned and BYOD devices.
Research by Kaspersky showed that attacks on mobile devices increased by 50% compared to the previous year, reaching almost 33.8 million attacks. The UK accounted for 258,959 of these attacks. The most common threat to mobile devices was adware, accounting for 40.8% of the detected threats.
Trend 9. Evolution of Social Engineering Attacks
Social engineering is the manipulation of individuals to extract sensitive information, such as passwords or personal data, from an organisation, often through impersonation.
Social engineering attacks continue to evolve in sophistication, leveraging psychological manipulation techniques to exploit human vulnerabilities and bypass traditional security measures.
From pretexting to baiting, cybercriminals are adept at deceiving users into divulging sensitive information or clicking on malicious links. To defend against these attacks, organisations must combine technical controls with comprehensive employee training and security awareness programs.
Some of the trending social engineering attacks in 2024 include QR phishing, SIM swapping, fake QR code scams, and MFA fatigue attacks.
Finance Director, High-Income Charity UK stated:
“Attacks are increasing during tough economic times. We need to be extra careful and alert to sophisticated social engineering attacks.”
More than 700 organisations fall victim to cyber incidents due to social engineering attacks each year. Surveys show that over 12 million spear phishing and social engineering attacks happened, affecting more than 17000 organisations. About 98% of cyber-attacks involve social engineering or phishing.
LookingGlass Cyber and ISACA say that social engineering attacks are the biggest cyber security threats in today's world.
Verizon reports that out of 2,249 social engineering attacks, 1,063 led to data being disclosed. In these cases, 24% of the leaked data was Personally Identifiable Information (PII).
ZDNet states that IT professionals encounter social engineering attacks an average of 40 times a year. Verizon also found that 69% of breaches in the Public Administration sector involve types of social engineering attacks.
However, only 27% of organisations provide training and awareness campaigns on social engineering.
Trend 10. Escalating Ransomware-as-a-Service (RaaS)
Ransomware attacks have become increasingly commoditised, with cybercriminals offering Ransomware-as-a-Service (RaaS) to less technically savvy actors in exchange for a cut of the profits. This trend is expected to accelerate in the coming years, fuelling a surge in ransomware attacks targeting organisations of all sizes.
To protect against ransomware in 2025, organisations should implement robust backup and disaster recovery solutions, implementing proactive security measures, threat detection and incident response capabilities.
James Babbage, Director General for Threats at the National Crime Agency, stated: "Ransomware remains a significant national security threat. As this report indicates, we expect the threat to grow in the coming years due to advancements in artificial intelligence and the ways cybercriminals are exploiting this technology."
By mid-2024, reported ransomware incidents in the UK have decreased by 15.2% compared to late 2023, with a global drop of 8%. This decline is notable despite evidence that ransomware groups are inflating attack numbers to appear more active.
While ransomware may seem to be slowing overall, specific threats in certain sectors, organisation sizes, and countries continue to persist.
Trend 11. 5G and IoT Security Challenges
The rollout of 5G networks and the proliferation of Internet of Things (IoT) devices are creating new security challenges for organisations, as these technologies introduce additional attack vectors and expand the surface area for potential cyber-attacks.
In the years ahead, organisations must prioritise 5G and IoT security, implementing measures such as network segmentation, device authentication, and encryption to mitigate the risks associated with these emerging technologies.
Trend 12. Efficient Third-Party Cybersecurity Management
Third-party vendors and suppliers play an integral role in the operations of many businesses, but they also pose significant cybersecurity risks.
The rising threat of cybersecurity incidents involving third parties demands that our security teams and leaders prioritise resilience over initial due diligence.
The growing risk of cybersecurity incidents affecting third parties is pushing security leaders to prioritise resilience over initial due diligence. Gartner recommends enhancing risk management for third-party cloud services and fostering strong partnerships with key external partners to safeguard valuable assets.
“Strengthen contingency plans for high-risk third-party engagements,” advised Gartner's management. “Create specific incident response playbooks, conduct tabletop exercises, and implement a clear offboarding strategy, including timely access revocation and data destruction.”
In 2024-2025, organisations will need to adopt more efficient third-party cybersecurity management practices, including vendor risk assessments, contractual obligations, and ongoing monitoring of third-party network security posture.
61% of organisations reported that they experienced a data breach or security incident involving a third party in the past year. This is a 49% increase compared to the previous year.
Trend 13. Enhancing Cybersecurity with Identity & Access Management (IAM)
Identity and Access Management (IAM) solutions are critical components of a robust cybersecurity strategy, enabling organisations to manage user identities and control access to sensitive resources.
In the coming years, we expect to see increased adoption of IAM solutions, including multifactor authentication, single sign-on, and privileged access management, to strengthen security posture and streamline access controls.
UK Statistics shows:
A significant 80% of cyberattacks rely on identity-based attack methods, highlighting the crucial role of user identities in these security threats. (CrowdStrike)
An overwhelming 99% of security decision-makers anticipate that their organisations will experience an identity-related breach within the next year, underscoring the urgency of addressing identity security. (CyberArk)
The average financial impact of a data breach is a staggering $4.45 million, emphasising the serious consequences organisations face when their data security is compromised. (IBM)
According to three out of four Chief Information Security Officers (CISOs), collaboration tools introduce substantial new security risks. Furthermore, 94% believe that the built-in security features of Microsoft 365 are inadequate to protect against these cyber threats effectively. (Mimecast)
A notable 80% of security professionals assert that improved identity and access management practices could have prevented some or even all of the attacks faced by their organisations, highlighting the importance of effective identity security measures. (One Identity)
Trend 14. Addressing the Cybersecurity Skills Shortage
The cybersecurity skills shortage remains a significant challenge for organisations worldwide, with a growing gap between demand and supply of qualified cybersecurity professionals.
To address this shortfall, security leaders must invest in cybersecurity education and training programs, mentorship initiatives, and workforce diversity efforts to cultivate the next generation of cyber defenders.
93% of UK businesses report an IT skills gap, according to a survey of 500 companies.
Many attribute this issue to the rapid pace of technological advancements, particularly in areas like artificial intelligence, data analytics, and cloud computing, with 42% citing this as a factor.
Training and development challenges are also significant, as 41% mention a lack of training opportunities, and 37% highlight the absence of relevant educational programs.
Additionally, 35% of businesses see competition in the job market as a challenge, with a limited number of skilled candidates making recruitment difficult.
Lastly, 29% point to salary disparities as a factor, as higher-paying industries attract IT professionals away from tech roles.
Trend 15. Cloud Security: Common Problems and Fixes
.png?width=1080&height=1080&name=API%20Security%20Statistics%202023%20(Strategi%20cyber%20trends).png)
As organisations continue to migrate their workloads to the cloud, cloud security remains a top priority. Common cloud security challenges include misconfigurations, data breaches, and unauthorised access.
To enhance cloud security posture, organisations should implement robust cloud-security measures, including encryption, access controls, and continuous monitoring, to protect against emerging insider threats, and compliance requirements.
What will the future cyber security trends be for 2025?
Cybersecurity will be very important in 2025 as we rely more on digital technology. This field protects our networks, devices, and data stored in the cloud. Because of this, there will be a high demand for cybersecurity professionals.
Here are just a few predictions for 2025:
- Increased Automation & Artificial Intelligence
- Improved Collaboration & Cyber Security Analytics Through BI tools
- The Rise of Machine Learning
- Cloud Security Gets a Boost
- Greater Focus on Security Awareness and Training
How to keep your business safe in 2024?
Organisations must stay informed about the latest cyber threats to protect themselves.
Here are some tips for keeping your business safe in 2024:
1. Use Multi-Factor authentication (MFA)
MFA requires users to enter two or more pieces of information when logging into an account, such as a combination of passwords and biometric identification. Implementing this will ensure the highest level of security for your business.
2. Update your software
Outdated software can be a major security risk, as malicious hackers may use vulnerabilities in older versions to gain access. Make sure all your systems are running the latest version of their respective software.
3. Invest in cybersecurity solutions
Consider investing in several different cybersecurity solutions, such as malware scanners and firewalls, which can help protect against various threats.
4. Educate yourself and your employees on cyber safety
Encourage everyone at your business to stay updated with current best practices in cybersecurity and data protection. This includes protecting passwords, avoiding clicking on suspicious links and emails, using secure Wi-Fi, and more.
5. Monitor your systems
Keep an eye on all your business's networks and systems for any suspicious activity or unusual network traffic. If you notice anything, investigate further to ensure that it is not a cyber-attack.

By following these tips, you can ensure that your business is safe from data breaches, and other security risks and updated for cybersecurity trends in 2025.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)

-2.png?width=1366&height=768&name=Blog%20Hero%20Banners%20(4)-2.png)
-2.png?width=1366&height=768&name=Blog%20Hero%20Banners%20(5)-2.png)






