What are the changes to Cyber Essentials and Cyber Essentials Plus in the April 2025 update?
Cyber Essentials is a government-supported program designed to help organisations (startups, SMEs, or enterprises) defend against cyberattacks.
The IASME (Information Assurance for Small and Medium Enterprises) recently released updated cyber essentials requirements for the IT infrastructure document (version 3.2), the Question Set (Willow), and the Cyber Essentials Plus Test Specification document (version 3.2) in advance to allow for preparation for any applications submitted on or after April 28th, 2025.
This blog post will provide a detailed guide to the changes to Cyber Essentials in 2025. This will assist organisations seeking the Cyber Essentials certification in understanding any planned updates to the scheme.
Also, at the end of the blog, you can find all the important links to IASME and NCSC’s Cyber Essentials and Cyber Essentials plus documents.
Key Changes:
|
Cyber Essentials Requirements for IT Infrastructure document v3.2
Willow Question Set Cyber Essentials Plus Test Specification document v3.2
|
When Will the Changes to Cyber Essentials Be Effective?
Effective 28th April 2025, the Cyber Essentials requirements for IT infrastructure v3.2 document, Question Set (Willow), and Cyber Essentials Plus Test Specification v3.2 document will come into effect.
Starting from this date, all new Cyber Essentials and Cyber Essentials Plus applications will be assessed using the Willow Question Set instead of the Montpellier Question Set that is currently in use.
 Source: IASME
Source: IASMEWhat's New in the Cyber Essentials Requirements for IT Infrastructure Document?
As technology continues to advance rapidly, it's crucial for Cyber Essentials requirements to adapt and change to stay relevant and effective.
Here are the changes to the Cyber Essentials requirements for IT infrastructure v3.2 document:
1. Passwordless Authentication Added to User Access Control
The Cyber Essentials requirements were updated in 2022 to mandate the use of multi-factor authentication for all accounts and services available over the internet, in response to the vulnerability of passwords.
But, considering the evolving changes in cybersecurity, the 2025 update introduces a new technology for accessing accounts.
Therefore, in the new version, passwordless authentication technology is added under the “User Access Control” section.
Moreover, instead of typing in a password, you should use other, more secure methods to prove your identity. Passwordless systems work by using something you have (like a phone or security key) or something you are (like a fingerprint or face scan).
Passwordless authentication is becoming more popular because of better security, no more password fatigue, faster login experience and reduced password management.
As per the updated Cyber Essentials Requirements for IT Infrastructure v3.2 document, passwordless authentication is defined similarly to multi-factor authentication (MFA).
The definition states “Passwordless authentication is a method that uses factors other than user knowledge to establish identity, such as biometric data, physical devices, one-time codes, QR codes, and push notifications.”
Some common methods of passwordless access are:
Biometrics
When you use a fingerprint or face scan, your device checks the unique traits of your body to verify that it’s you. Your phone or computer can scan your fingerprint to confirm your identity. Systems like Apple’s Face ID scan your face and compare it with stored data to log you in.
One-Time Codes
When you log in, you receive a temporary code on your mobile phone or email. You enter this code, and it proves you are the rightful user. Also, apps like Microsoft Authenticator generate a time-sensitive code you can use for login.
QR Codes
QR code-based authentication involves scanning a unique code to confirm your identity. When you attempt to log in, a QR code appears on the screen. You scan it with your smartphone, and the system verifies your identity. This method is secure because it ties your device to the login session, making it difficult for others to access your account without your phone.
Physical Devices
These are security keys or tokens such as USB security keys or smart cards plugged into your computer or phone. They send a signal to verify your identity, allowing you to log in without a password. Physical devices are extremely secure, as they require the actual hardware to be in your possession for authentication.
Push notifications
Push notifications are another modern method of passwordless authentication. When you try to log in to an account, a notification is sent to your phone. You simply tap “Approve” or “Deny” confirming your identity. This method is quick and convenient because you don’t need to type anything—just approve the request on your mobile device.
2. Software Definition Updated
In the Cyber Essentials update 2025, the software definition includes the term ‘extensions’ for improved accuracy in place of the term ‘plugins’.
As per the updated Cyber Essentials Requirements for IT Infrastructure v3.2 by NCSC, the software definition states, “Software includes operating systems, commercial off-the-shelf applications, extensions, interpreters, scripts, libraries, network software and firewall and router firmware”.
For a clearer picture, refer to the screenshots below:

version v3.1
 version v3.2
version v3.2Source: NCSC
3. Vulnerability Fix Added to Security Update Management Control
In the rapidly changing digital environment, vulnerabilities in software are routinely exploited by malicious individuals or groups to launch attacks on computers and networks.
So, addressing vulnerabilities isn't just about installing a patch or update. It's a comprehensive process that involves several steps including vulnerability assessment, patch management, testing the fix, deployment of the fix and post-patch monitoring and reporting.
Since there was a requirement change regarding patching and updating software in the security update management section, the term 'vulnerability fixes' needed to be described in the updated version.
In the context of Cyber Essentials, the concept of vulnerability fix refers to the critical process within security update management that aims to identify and rectify potential weaknesses within devices and software systems. This proactive approach helps ensure that known security issues, for which fixes are available, are promptly addressed to safeguard against potential cyber threats.
In the Cyber Essentials updated document, the third-party software providers should adhere to the highest security standards, as vulnerabilities in third-party apps can compromise your entire infrastructure.
As a result, the provider should address any vulnerabilities found in the products they still support. This can be done through patches, security updates, registry fixes, scripts, configuration changes, or any other method recommended to fix a known vulnerability.
In the new version of the Cyber Essentials requirements document, i.e. v3.2, the term 'patches and updates' has been changed to 'vulnerability fixes' to encompass all different methods.
As per the updated Cyber Essentials Requirements for IT Infrastructure v3.2 by NCSC, the vulnerability fix definition states “Vulnerability fixes include patches, updates, registry fixes, configuration changes, scripts or any other mechanism approved by the vendor to fix a known vulnerability”.
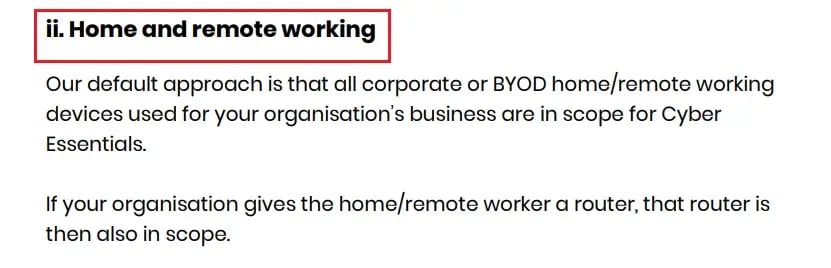
4. 'Home Working' Changed to 'Home and Remote Working'
In the earlier version of Cyber Essentials Requirements for IT Infrastructure v3.1, the term home working was mentioned (refer to the screenshot below).

In the updated version v3.2, the reference changed to home and remote working (mentioned in the below screenshot):
 Source: NCSC
Source: NCSCWhen we talk about 'remote' working, we understand that it's not just about working from home. In simple terms, remote work means working anywhere outside the office premises. It also includes working in public places like hotels, trains/buses, cafeterias and other shared spaces where the network may not be secure.
The Cyber Essentials standard includes all devices used for your organisation's business, whether they are company-provided or personal devices (BYOD) used for work. If your organisation provides a router to a home or remote employee, that router is also included.
Cyber Essentials firewall controls, such as a software firewall, need to be applied to users' devices if they are using their own router. If the home or remote staff uses a corporate VPN, their internet connection is protected by the virtual or cloud firewall.
What's Updated in the Cyber Essentials Plus Test Specification v3.2?
This document is mainly for personnel who perform Cyber Essentials Plus assessments for Certification Bodies (referred to as the 'Assessor' or 'you').
It may also be useful for organisations seeking the Cyber Essentials Plus certification (referred to as the 'Applicant'). Staff involved in the process may want to understand the test criteria that form the assessment.
1. Document renamed
The earlier version of Cyber Essentials Plus Illustrative Test Specification v3.1 consisted of the word ‘illustrative’ in the document name. You can refer to the below screenshot.

The word, ‘illustrative’ has been dropped from the name of the Cyber Essentials Plus test specification document in the new version v3.2 as shown in the below screenshot.
 Source: NCSC
Source: NCSC2. Verification of scope added
The second pointer under the ‘Before you begin’ section mentioned in the Cyber Essentials Plus test specification v3.1 document has been replaced with ‘verification’ pointers in the test specification v3.2 new document.
In the updated Cyber Essentials Plus test specification v3.2 document, the ‘verification of scope’ pointer is added.
It states that “Before commencing testing, it is crucial to verify that the scope of the Cyber Essentials Plus assessment aligns with the scope outlined in the valid Cyber Essentials self-assessment certificate and networks and system being assessed and be verified by the Assessor.”
3. Verification of segregation by sub-set added
In the updated Cyber Essentials Plus document, the verification of segregation by sub-set is added in the fourth pointer.
It states that:
“Before you begin the testing process, it is essential to confirm that if the Cyber Essentials self-assessment scope is not the entire organisation, and the Assessor must verify that any subsets have been properly segregated using technical methods.”
You can refer to the below screenshot:
 Source: NCSC
Source: NCSC4. Verification of sampling added
Finally, the last update in the Cyber Essentials Plus document v3.2 is the verification of sampling added to the fifth point. You can refer to the screenshot above.
It states that:
Make sure to take the necessary steps to ensure that your sample of devices, including servers and EUDs, is representative before starting the testing process.
Many organisations use standardised configurations for their servers and EUDs, which means that a small number of representative samples can cover much of the organisation's equipment.
In addition, the NCSC recommends ensuring that your testing covers all relevant devices. The number of devices you need to test will depend on the variation caused by the Applicant's provisioning processes and their effectiveness.
The assessor must confirm that the sample size has been calculated correctly using the method described by the IASME.
Also, the Certifying Body must keep evidence of how the sample size was calculated for at least the lifetime of the certificate.
How can Aztech help?
As a trusted cybersecurity partner and accredited certification body, Aztech will guide you through the process of achieving your Cyber Essentials or Cyber Essentials Plus certification with expertise and personalised support.
Throughout the certification process, Aztech will offer guidance, training, and documentation support to empower your team with the knowledge and tools needed to strengthen your cybersecurity defences effectively.
Summary
In conclusion, the April 2025 update to Cyber Essentials and Cyber Essentials Plus, managed by IASME, introduces key changes to better adapt to the evolving cybersecurity landscape. The update includes enhancements to the IT infrastructure requirements, the Willow question set, and the Cyber Essentials Plus test specification.
The Cyber Essentials requirements for IT infrastructure key changes include the introduction of passwordless authentication technology, a refined definition of software (replacing "plugins" with "extensions"), reference change from ‘home working’ to ‘home and remote working’, and addition of vulnerabilities fixes to security update management control.
Additionally, updates to the Cyber Essentials Plus test specification document include new guidelines added for verification of scope, segregation by sub-set, and sampling to ensure accurate testing with the Applicant's compliance with the technical requirements of the Cyber Essentials scheme.
So, all the changes to Cyber Essentials will be effective April 28, 2025, and all the applications will be assessed against these updated standards, helping you to strengthen your cybersecurity defences.
For more information, you can contact us or schedule a one-on-one call with one of our experts.
Important Links to Cyber Essentials Changes 2025
Cyber Essentials Question Set and Standard
Cyber Essentials: Requirements for IT Infrastructure v3.2

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)