Understanding the difference between a Next-Generation Firewall (NGFW) and a Traditional Firewall is important when securing your network.
Firewalls are the first line of defence of network systems, which helps to keep out unwanted traffic. Not all firewalls are equal and over time, firewalls have evolved to meet the growing challenges of modern cybersecurity.
The traditional firewall handles basic tasks like filtering traffic based on an IP address or port. However, as cyber-attacks have advanced, a new solution has emerged—the Next-Gen Firewall (NGFW).
In 2022, the UK's next-generation firewall market made £1 million in revenue. By 2030, it is expected to reach £2.5 million.
With the advancements in cloud computing and firewall technology, businesses now face a choice: next-gen firewall vs traditional firewall. Both have their strengths and serve different purposes, but which is right for your business?
In this blog post, we will explore how a Next Generation Firewall (NGFW) differs from traditional firewalls and why upgrading might be the smarter choice for your business.
Key Takeaways:
-
The primary function of a Next-Generation Firewall (NGFW) is to provide advanced security features, including deep packet filtering, application control and integrated IPS.
-
In contrast, a traditional firewall functions to perform packet filtering and stateful packet inspections based on IP, port, and protocol.
What is a Next-Generation Firewall (NGFW)?
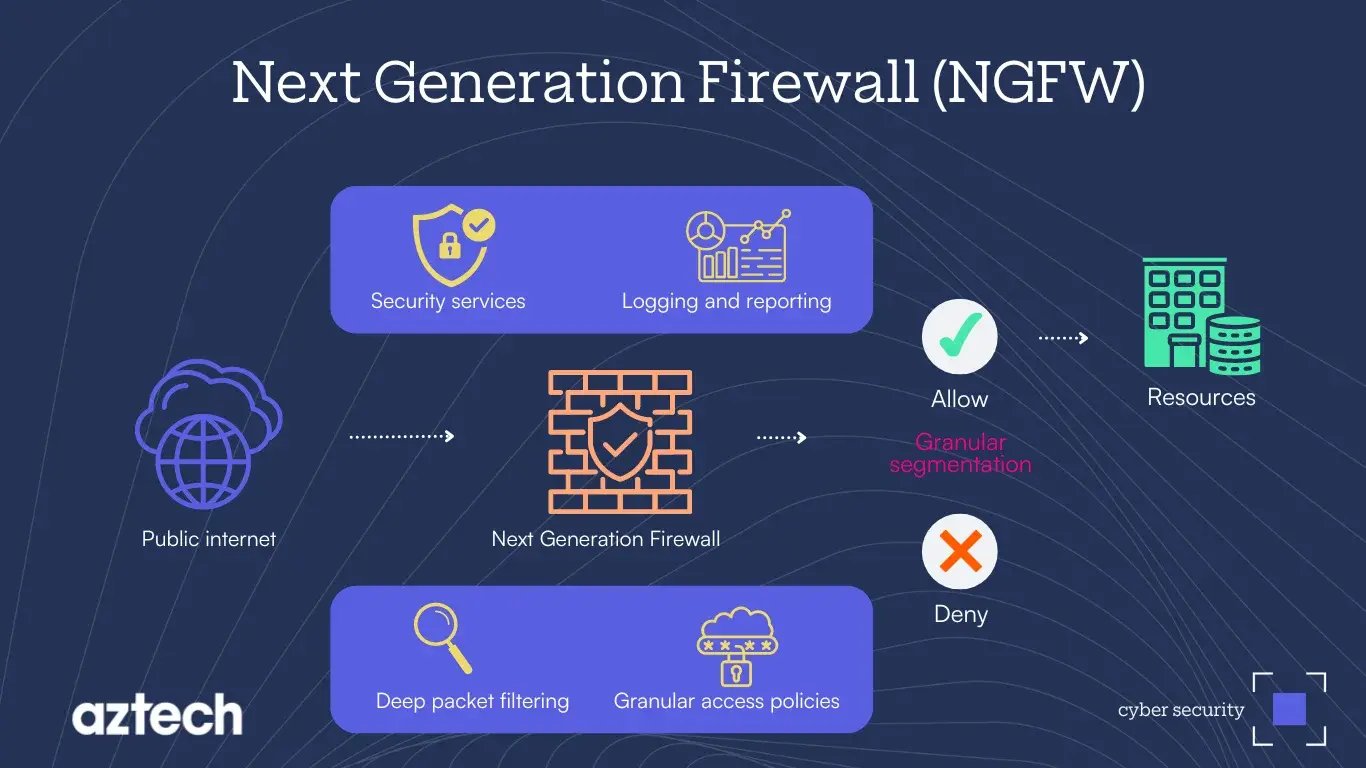
A next-generation firewall (NGFW) is a modern network security device designed to protect business networks against advanced cyber threats like advanced persistent threats (APTs) and zero-day attacks.
Unlike traditional firewalls, NGFWs provide deeper control over network traffic and security services by going beyond basic packet filtering and stateful inspection with features like deep inspection, integrated IPS, application awareness and control.
Key Features of a Next-Gen Firewall
-
Deep Packet Inspection (DPI): NGFWs use deep inspection to thoroughly analyse the content of data packets, allowing it to detect and block malicious traffic that may slip through traditional firewalls.
-
Integrated Intrusion Prevention System (IPS): A built-in IPS actively scans traffic for signs of attack and takes immediate action to block malicious activity.
-
Application Awareness and Control: NGFWs can identify and manage applications (such as social media platforms or cloud services) running over the network, even if they use non-standard ports.
-
Threat Intelligence Feeds: They utilise threat intelligence from global sources to stay updated on emerging threats, giving them the ability to block new attack patterns and provide real-time protection.
-
Encrypted Traffic Inspection: NGFWs can decrypt any encrypted traffic, inspect it for threats, and re-encrypt it to ensure privacy without sacrificing security.
What is a Traditional Firewall?

A traditional firewall is a basic security device that filters traffic based on predefined security policies and rules. It analyses IP addresses, port numbers, and protocols to decide whether to allow or block specific traffic.
A traditional firewall can perform a stateful or stateless inspection. In stateless inspection, the firewall looks at each packet individually using static information like source and destination. On the other hand, stateful firewalls examine the entire context of the network connection, which provides higher security.
Moreover, a traditional firewall can track the state of active and outgoing network traffic and connections and filter traffic based on administrator-defined rules tied to the connection state.
Key Features of Traditional Firewalls
-
Standard Packet Filtering: The Traditional firewall solution provides standard packet inspection, examining the header information of incoming and outgoing packets. They allow or block traffic based on source and destination IPs, ports, and protocols.
-
Stateful Inspection: These stateful firewalls can remember active connections and decide whether new packets are part of a known, legitimate connection.
-
Network Address Translation (NAT): These firewalls often include NAT functionality, allowing devices on a private network to communicate with external networks by masking internal IP addresses.
-
Limited Application Control: These firewalls cannot control applications running over the network, focusing mainly on basic traffic management.
Next-Gen Firewall (NGFW) vs Traditional Firewall: Which One Should You Choose?
1. Stateful or Stateless Inspection
A traditional firewall relies on stateful or stateless inspection, which tracks the state of active connections and filters traffic accordingly.
NGFWs, on the other hand, enhance this feature by incorporating advanced techniques like DPI allowing for more thorough analysis and blocking of harmful traffic.
2. Packet Filtering
While both types of firewalls perform packet filtering, traditional firewalls provide basic protection through standard packet inspection, only looking at header information like destination IP and ports.
Next-generation firewalls go deeper by inspecting the contents of packets to detect threats that may bypass simple filters.
3. Intrusion Prevention System (IPS)
One of the key advantages of NGFWs is their built-in IPS, which is capable of actively blocking intrusions and blacklisting all future traffic from known threats, including advanced persistent threats and zero-day vulnerabilities.
A traditional firewall does not have IPS capabilities, leaving networks more vulnerable to advanced threats.
4. Threat Intelligence
NGFWs leverage global threat intelligence feeds to stay updated on the latest threats and provide real-time protection.
A traditional firewall generally lacks this capability, offering standard protection without appropriate security measures, against emerging cyber threats.
5. Working Layer
Traditional firewalls typically operate at the network layer (Layer 3) of the Open Systems Interconnection (OSI) model - Physical layer, Data Link Layer, Network Layer and Transport Layer, focusing on traffic routing and basic filtering.
NGFWs, in contrast, operate on multiple layers, including the application layer (Layer 7), offering granular control over the traffic and better protection against advanced threats.
6. Application Awareness
Application level control is a critical feature that allows NGFWs to identify and control specific applications within network traffic.
Traditional firewalls lack this capability, limiting their ability to manage modern web-based services and applications effectively.
7. Virtual Private Networks (VPNs)
Both NGFW and traditional firewalls allow a virtual private network to keep internet users on a private network secure when using the internet.
However, NGFW offers enhanced VPN features with better control and monitoring of encrypted traffic compared to the traditional ones.
8. CAPEX and OPEX
Traditional firewalls tend to have lower CAPEX (capital expenditure) and OPEX (operating expenses) compared to NGFWs.
However, businesses requiring deeper protection against modern threats might find the higher upfront and operational costs of NGFWs justified due to their advanced features.
9. Network Address Translation (NAT)
Both types of firewalls support Network Address Translation (NAT), helping to maintain private network security by masking internal IP.
However, NGFWs offer more advanced NAT capabilities for complex, modern networks.
10. Reporting
A next-generation firewall provides more detailed and actionable reporting than a traditional firewall.
NGFWs can pull customised reports and offer insights into application usage, user behaviour, and security policy enforcement, whereas the traditional one typically offers limited logging and basic reporting of security functions only.
 Summary
Summary
Next-gen firewalls provide deeper protection with advanced features like deep packet inspection, application control, and IPS, making them a robust choice for businesses facing evolving threats.
On the other hand, traditional firewalls offer basic traffic filtering (Port, IP Address, and Protocol-based) and are suitable for simpler networks that need basic protection.
Therefore, if your business faces advanced threats or requires application control and DPI, a Next-Generation Firewall is essential. For standard packet filtering and simpler networks, a traditional firewall offers sufficient protection at a lower cost.
Ultimately, the right choice depends on your network’s complexity, security needs, and budget.
Whether you need to block advanced threats, ensure secure network communication through VPNs, or handle basic packet filtering, understanding the differences between NGFW and traditional firewalls will help you make an informed decision.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)






-3.png?width=536&name=Blog%20Hero%20Banners%20(4)-3.png)
