Have you ever heard of a SIM Swapping Attack?
It's an increasingly popular type of cybercrime in 2023 that affects thousands of individuals and businesses every year, often resulting in financial loss.
SIM swapping, also known as a sim swap scam, SIMjacking or SIM hijacking, SIM splitting and port out scam, is a technique to get access to your mobile phone number and personal information without your permission or authorisation.
In this blog post, we will explain exactly what a SIM swapping attack is, how it works, and explore ways to prevent such attacks from happening or protect yourself if you become a victim.
What is a SIM?
To better understand SIM swapping, we first need to know about the chip which we insert into our mobile phones, what it does and how it leads to SIM hijacking.
A SIM card, or Subscriber Identity Module, is a small removable card that is inserted into a cell phone or other device to identify the user to the cellular network.
In addition, it contains a unique identification number and other personal information, such as contacts and messages.
Also, the SIM card stores the user's plan information, such as phone number and data allowance.
So, the user information has been stolen by the fraudsters.
Now, let's see what exactly SIM swapping is.
What is SIM Swapping?
SIM swapping is a term used to describe a type of fraud where scammers take control of your phone number by exploiting security loopholes in the way mobile networks operate.
In simple terms, a SIM swap scam is a fraudulent method used to take over someone's account.
So, it specifically targets a vulnerability in two-factor authentication and two-step verification, where the second factor or step involves sending a text message (SMS) or make calls.
Once they have gained control, the scammers can intercept all your phone calls and text messages, including those containing sensitive information like your banking details or password resets.
They can then use this information to steal your identity, access your online accounts and carry out various types of fraudulent activity.
What is a SIM Swap Attack?
SIM swap attacks also known as a port-out scam, is a type of fraud which involves fraudsters tricking a mobile carrier into transferring a victim's phone number to a new SIM card in their possession.
Once the attackers have access to the victim's phone number, they can take control of their online accounts, such as bank accounts, email addresses, and social media accounts.
Now, let's understand how a SIM card scam works.
How Does a SIM Swapping Scam Work?
This is how SIM swapping works:
Step 1: Obtaining your phone number
The first step in this scam is for the criminal to obtain your phone number. This can be done by either stealing your SIM card or by “phishing” you – sending you an email that looks like it’s from a legitimate source but contains malicious links or attachments.
Step 2: Requesting service providers to transfer cell phone number
Once the criminal has obtained your phone number, they will contact your mobile service provider and request them to transfer the number to a new SIM card.
This process is known as “SIM swapping” and is surprisingly easy for criminals to do, as many mobile carriers do not have robust security measures in place to prevent this type of fraud.
Step 3: Taking full control of your phone number
Once the criminal has control of your phone number, they can then use it to reset passwords on accounts such as online banking and social media, allowing them to take advantage of accessing it without needing any additional authentication such as security questions and two-factor authentication or SMS codes.
Recent Examples of SIM Swapping Incidents in UK
Financial Advisory Kroll – SIM Swapping Incident
The latest example of a sim swap attack was encountered by a financial advisory firm, Kroll.
On Saturday, August 19, 2023, a cyber threat actor executed a highly sophisticated "SIM swapping" attack targeting a T-Mobile US., Inc. account linked to a Kroll employee.
Without any authorisation or communication with Kroll or its employee, T-Mobile transferred the employee's phone number to the threat actor's device upon request.
Consequently, the threat actor obtained access to specific files containing personal information of bankruptcy claimants associated with BlockFi, FTX, and Genesis.
Immediate measures were implemented to secure the three affected accounts and affected individuals have been notified via email.
You can read about the Kroll sim swap scam here.
NatWest Bank SIM Swap scam
The NatWest Bank sim swap scam was initially exposed by BBC Radio 4’s You and Yours program.
The investigation was prompted by numerous complaints from victims of similar schemes.
Here's how the scam worked: criminals start by reporting the victim's sim card or phone number as lost or stolen to their mobile carrier.
They then request the mobile phone carrier that the victim's mobile number be transferred to one of their own SIM cards.
This allows the criminals to conveniently receive SMS messages meant for the victim.
Subsequently, the criminals contact NatWest and pretend to have forgotten their online login details such as customer ID number, password, or PIN.
While NatWest cannot immediately provide this information, in compliance with its Two-Factor Authentication policy, it sends a code via text message to the victim's number.
The criminals can then use this code on NatWest's website to reset the password and PIN, ultimately gaining control of the victim's bank account.
You can read the complete NatWest bank sim swapping incident here.
Tesco Bank SIM Swap Incident
On a recent episode of Rip Off Britain, a victim of sim swap scams, Wendy Darby shared her personal experience of falling victim to SIM swaps fraud.
This malicious act not only violated her privacy but also resulted in scammers taking out loans in her name.
It all started back in February 2022, when Wendy was hosting a dinner party and received unexpected texts from her phone provider, Tesco Mobile, confirming a new SIM card request.
Initially, Wendy dismissed it, thinking it was a mistake.
However, things took a turn for the worse when her phone lost service and continued causing problems the next morning.
The fraudsters had not only gained access to her phone but also managed to infiltrate other bank accounts.
To make matters worse, the criminals obtained a £23,000 loan in Wendy's name, and even applied for an additional £17,000 loan with a bank she wasn't even associated with.
In response to this incident, a Tesco Mobile spokesperson emphasised their commitment to customer protection, implementing measures such as automated text verifications for SIM swap requests.
If a request is found to be fraudulent, customers can cancel it while their Fraud Team investigates the matter.
You can read about the complete Tesco bank sim swapping incident here.
How To Know If You Have Been SIM Swapped?
Here are the 4 signs to know if you are a victim of SIM swap attack:
1. Unusual Activity
One of the first signs of a SIM swap attack is unusual activity on your phone.
If you suddenly start receiving phone calls, texts, or emails from unknown numbers or unfamiliar contacts, it is possible that someone has gained access to your phone number and is using it for their own purposes.
Additionally, if you notice any changes in your phone's service or settings, this could be an indication that someone has tampered with your phone.
2. Unauthorised Purchases
Another sign of SIM swap scams are unauthorised purchases made with your credit card or other payment methods linked to your phone number.
If you notice any charges on your account that you did not make, it is important to contact your bank or credit card company right away to report the issue and investigate further.
3. Suspicious Text Messages
If you receive suspicious text messages from unknown numbers asking for personal information such as passwords or banking details, this could be an indication of a SIM swap fraud attempt.
It is important not to respond to these messages and instead immediately contact phone service providers so they can investigate the issue further.
4. Loss of Service
Finally, if you suddenly experience a loss of service on your phone, this could also be a sign of a SIM swap fraud.
If someone has gained access to your phone number and swapped out the SIM card associated with it, then they may have disabled the service on your device in order to prevent you from being able to use it.
If this happens, it is important to contact your mobile carrier right away so they can investigate the issue further and help restore service on your device.
How to Prevent SIM Swap Attacks?
Here are the 7 ways to avoid and what to do after being a victim of a SIM swap fraud:
1. Use Strong Passwords
One of the most important steps you can take to prevent SIM card swap fraud is to set strong passwords, pin codes and security questions for all your online accounts.
Make sure that your passwords are at least 8 characters long and contain a combination of uppercase and lowercase letters, numbers, and symbols.
Additionally, it is important to avoid using the same password and security questions for multiple accounts.
2. Enable Two-Factor Authentication
Another way to protect yourself from SIM swaps is to enable two-factor authentication (2FA) on all your online accounts.
With 2FA enabled, you will be required to enter a one-time code in addition to your username and password when logging into an account.
This code is typically sent via text message or email and can help prevent unauthorised access even if someone has obtained your login credentials.
3. Monitor Your Accounts Regularly
It is also important to regularly monitor your online accounts for any suspicious activity or changes in settings.
If you notice any unusual activity, do contact your service provider immediately so they can investigate further and act if necessary.
4. Keep Your Phone Secure
One way that scammers may try to gain access to your phone number is by stealing or hacking into your device itself.
To prevent this from happening, make sure that you always keep your phone secure with a passcode or biometric lock such as facial recognition or fingerprint scanning technology.
Additionally, consider investing in a good antivirus program for added protection against malicious software designed to steal personal information from your device.
5. Don’t Share Personal Information Online
Be cautious about what personal information you share online as scammers may use this information to gain access to your accounts or impersonate you to commit fraud or identity theft.
If possible, avoid giving out sensitive information such as social security numbers, bank account details, or credit card numbers over the internet.
6. Be Wary of Unsolicited Calls and Texts
Scammers often use phishing tactics such as unsolicited phone calls and messages to get people to reveal their personal information willingly or unknowingly provide them with access codes needed for SIM card swaps.
If you receive any suspicious calls or emails asking for personal information, do not respond and instead contact the company directly through an official channel such as their website or customer service line.
7. Report Suspicious Activity Immediately
Finally, if you think that someone has attempted a SIM swap attack on you or suspect that someone may be trying to gain access to one of your accounts without authorisation, contact law enforcement immediately so they can investigate further and act if necessary.
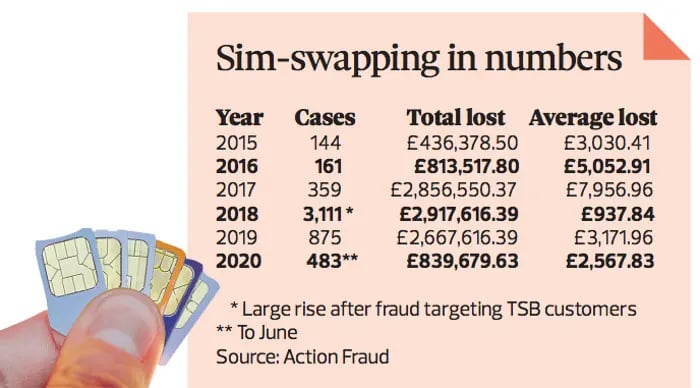
If you are in England, Wales or Northern Ireland you should report a SIM swap fraud to Action Fraud.
How Social Media Plays an Important Role in SIM Swap Fraud?
SIM hijacking heavily relies on gathering extensive personal data about individuals. Social media accounts are often goldmines of information that scammers exploit to successfully execute a SIM swap.
SIM swap fraud scammers go through social media accounts to uncover clues that aid them in hijacking phone accounts.
For instance, they might discover a pet's name from an Instagram post or the name of someone's high school from their Facebook groups.
If these details are used as passwords or answers to security questions, scammers can employ them to complete a SIM swap or gain control over accounts on a SIM they have access to.
Furthermore, it is worth considering that sometimes SIM attacks are carried out specifically to hijack someone's social media account and create malicious posts, leading to problems or embarrassment for the targeted individual.
A notable case occurred in 2019 when former Twitter CEO Jack Dorsey fell victim to a SIM swap, allowing fraudsters to send offensive messages through Dorsey's Twitter account using Cloudhoppers text-to-tweet function, all from his phone number.
The fraudsters posted offensive messages, some originating from the @jack account itself and others retweeted from different accounts, contained racial slurs, anti-Semitic remarks regarding the Holocaust, and even a bomb threat directed at the social media company's headquarters.
SIM Swap Attacks FAQs
What does a SIM swap do?
By intercepting messages or calls meant for your phone number, the fraudulent can impersonate you and potentially access your bank accounts, social media accounts, and other sensitive data.
How does a SIM swap happen?
It involves convincing your cell phone carrier to transfer your phone number to a different SIM card - one that the hacker controls. This can be achieved through social engineering tactics, like tricking you into providing personal information or using phishing techniques, ultimately deceiving your carrier into making the switch.
What is an example of a SIM swap scam?
Most recent incident occurred on 19th August 2023, where a cyber threat actor carried out a remarkably sophisticated attack known as "SIM swapping." The target was a T-Mobile US., Inc. account that was associated with an employee from Kroll.
How often do SIM swap attacks happen?
The answer is alarming; SIM swap fraud occurs frequently and is on the rise, and it is estimated that millions of people have already fallen victim to this type of attack.
Can you stop SIM swapping?
One of the most effective ways to stop SIM swapping is to enable two-factor authentication (2FA) on all your accounts.
Does switching SIM cards transfer everything?
No, while switching your SIM card allows you to keep your phone number, contacts, and messages, other important data like photos and apps won't automatically make the move with you.

