The discussion around Zero Trust versus traditional perimeter security has become more significant in today's digital world, where cyber threats are a constant concern.
So, what sets zero trust apart from traditional security approaches?
Zero-trust continuously monitors everyone and everything trying to access resources, while the traditional approach trusts insiders once they're past the network security, allowing broader access without constant verification.
In simple terms,
-
Zero Trust Security: No trusted inner network, always verifying users/devices.
-
Traditional Perimeter Security: Trust within network boundary, broader access.
The zero-trust security market is expected to grow by 2031, with an unexpected CAGR between 2024-2031 compared to 2023.
In this blog post, we'll compare zero trust with traditional security and explain why zero trust is better for your organisation.
What is a Zero-Trust Security Model?
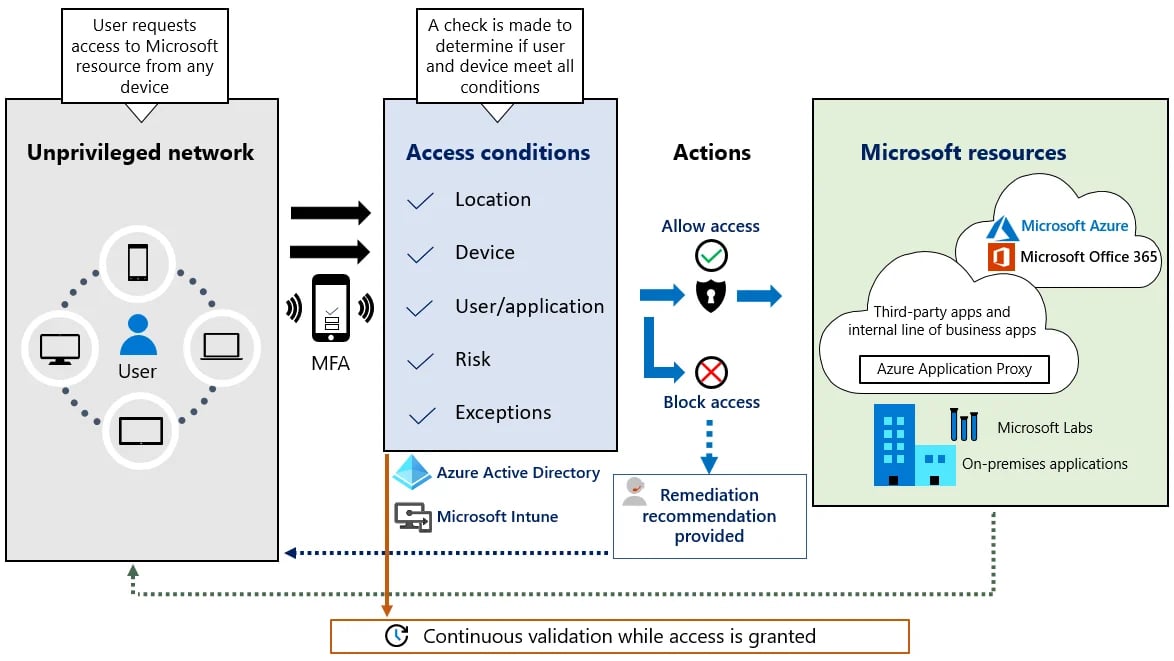
A Zero-Trust Security Model is a cybersecurity approach that assumes that nobody, whether inside or outside the network, should be trusted by default.
This means that no one is given the benefit of the doubt, and each user must prove their trustworthiness before gaining access to any network resources.
In a Zero-Trust model, granting access control is strictly enforced regardless of the user's location or the network they are connecting from.
Key Features of Zero Trust Principles
Here are some of the key features of zero-trust principles:
- Verify explicitly: In this, every single user and device attempting to gain access to the resources on the network must be authenticated and authorised, regardless of whether they are inside or outside the corporate network.
- Least privileged access: The zero trust approach uses the principle of least privilege to limit user access to reduce the potential damage in case of a security breach.
- Micro-segmentation: Zero trust networks are divided into smaller segments or secure zones to restrict the lateral movement of threats. Each segment has its user access controls and security policies.
- Continuous monitoring: The user and device behaviour is continuously monitored to help detect and respond to potential threats in real-time.
- Assume breach: Instead of assuming threats are external, the model assumes that attackers may already be present within the network, and security strategy should be designed accordingly.
Implementing a Zero-Trust Security architecture typically involves a combination of technologies such as multi-factor authentication (MFA), identity and access management (IAM), encryption, network segmentation, and security analytics.
By adopting this approach, organisations can enhance their security, reduce the risk of data breaches, and better protect sensitive data.
What is Zero-Trust Network Access (ZTNA)?
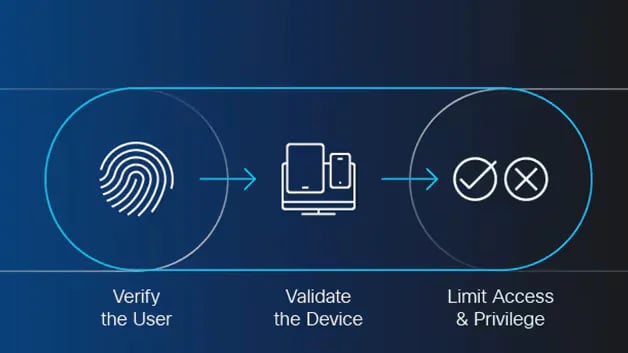
Zero-Trust Network Access (ZTNA) is an approach to network security that emphasises strict access controls and verification on a private network to ensure that users and devices can only access valuable data on a need-to-know basis, regardless of their location or network environment.
Unlike the traditional model, which relies on trusting entities within the corporate network, ZTNA requires authentication and authorisation to access sensitive data for each attempt.
ZTNA solutions can be of various types, including secure access service edge (SASE) platforms, software-defined perimeter (SDP) solutions, and identity-driven access control systems.
This helps organisations enforce zero-trust principles across diverse network environments, including on-premises networks, cloud services platforms, and remote endpoints.
Examples of Zero-Trust Security
Here are some common use cases where Zero-Trust Architecture proves to be beneficial:
1. Remote Workforce Security
Organisations should secure access requests of data, stored from various locations and devices.
This approach ensures that remote workers must authenticate and authorise themselves before accessing sensitive data or critical assets, regardless of location.
2. Cloud Security
As more businesses migrate their operations to cloud-based environments, ensuring the security of cloud resources becomes important.
The model helps gain access to cloud services by enforcing strict identity verification and access.
3. Partner and Vendor Access
Many organisations collaborate with external partners and vendors who require access to certain systems or data.
Zero-Trust Architecture enables organisations to securely grant access to third parties without compromising their internal security posture, by enforcing the same controls and verification mechanisms as for internal users.
4. Privileged Access Management (PAM)
Zero-Trust Architecture is crucial for managing and securing privileged accounts, which have elevated access privileges within an organisation's IT environment.
From executives to security teams, everyone should have the least amount of access they need. This minimises the risk of lateral movement within an organisation if an end-user account is compromised.
5. Data Centre Security
Zero Trust shifts the focus from network security to data-centric security.
Zero-Trust Architecture helps secure data centres by segmenting the network security and applying access control based on user identity, device security posture, and other contextual factors.
This ensures that only authorised users and devices can access specific resources within the data centre environment.
What is Traditional Perimeter Security Model?
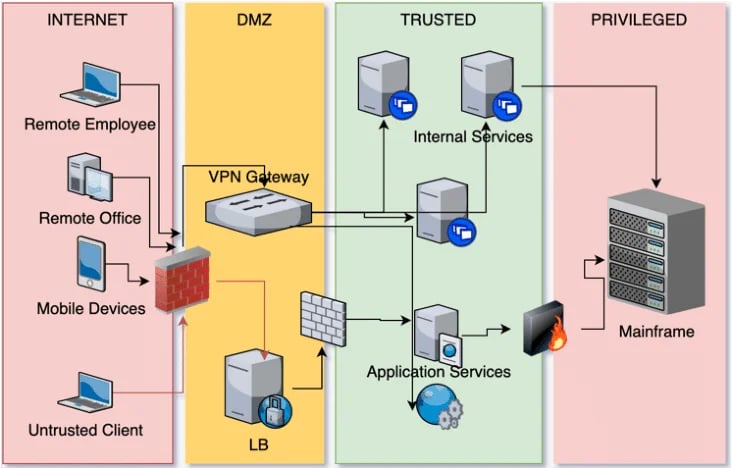
The traditional perimeter security model, also known as the castle-and-moat approach, relies on securing the network perimeter with firewalls and other security measures to keep external threats at bay.
Once inside the network traffic, users are granted unrestricted access to resources, fostering a false sense of security.
However, this model fails to address insider threats and lateral movement by cyber attackers once they breach the perimeter defences.
Advantages of a Zero-Trust Security Model
Implementing a Zero-Trust Model offers several advantages for organisations aiming to enhance their cybersecurity posture and adopt an effective security solution:
-
Improved Security Posture: By assuming that no entity, whether inside or outside the network, is inherently trusted, organisations can implement more robust security controls and protocols. This proactive approach helps mitigate the risk of data breaches and unauthorised access.
-
Minimised Attack Surface: Zero-Trust Architecture reduces the attack surface by strictly accessing controls and segmentation. Organisations can minimise the potential impact of security breaches by limiting access to resources based on user identity, device security posture, and other contextual factors.
-
Enhanced Data Protection: Zero-Trust Model emphasises data-centric security and focuses on protecting sensitive data such as personally identifiable information (PII), intellectual property (IP), and financial information.
-
Adaptability to Dynamic Environments: In today's dynamic IT environments characterised by cloud computing, remote work, and IoT devices, traditional perimeter-based security models are no longer sufficient. The zero-trust model provides a flexible framework that can adapt to changes in the network infrastructure, user behaviour, and emerging threats.
-
Reduced Insider Threats: Insider threats, whether intentional or accidental, pose a significant risk to organisational security. Zero-Trust Architecture can mitigate risk by implementing least privilege access, continuous monitoring, and behavioural analytics to detect and respond to malicious activities.
Zero Trust vs Traditional Perimeter Security: What’s the Difference?
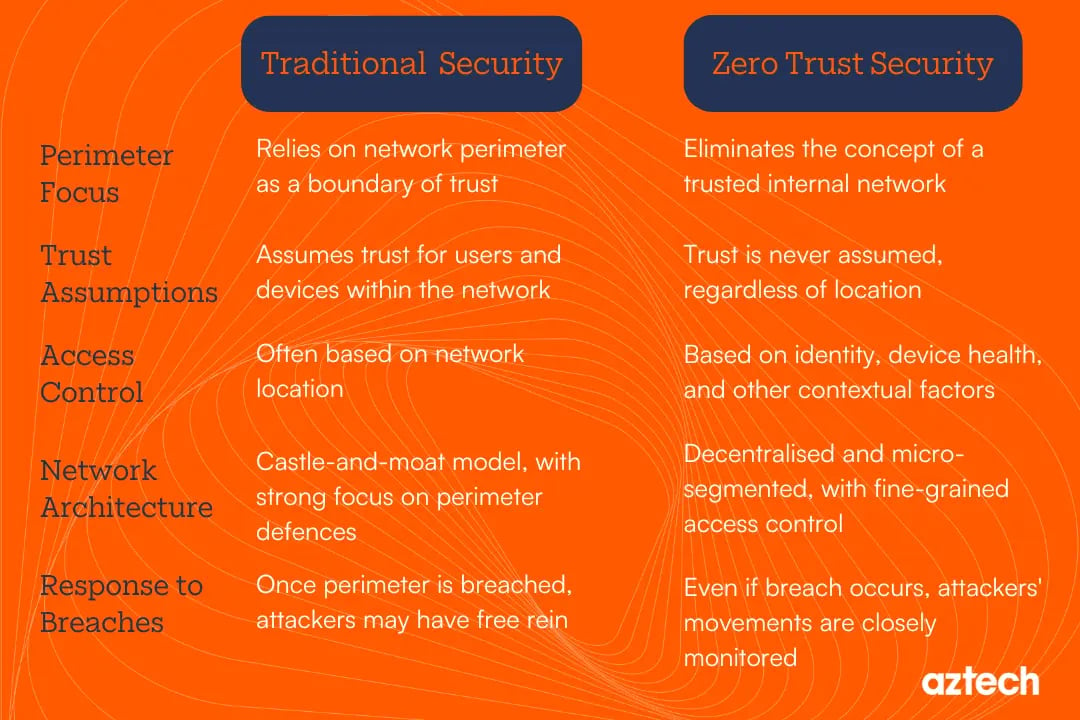
Here's a breakdown of the key differences between the two:
1. Perimeter Focus
The traditional model relies on the concept of a network perimeter, where there's an assumption of trust for devices and users within the network boundary. It often involves securing the network with firewalls, VPNs, and other boundary defences.
Zero Trust assumes that threats could be both external and internal, eliminating the concept of a trusted internal network. Instead of focusing on securing the perimeter, Zero Trust emphasises verifying every user and device attempting to connect to resources, regardless of their location.
2. Trust Assumptions
Trust is placed on users and devices within the network perimeter. Once inside, there's often less scrutiny and verification of their activities.
Trust is never assumed in a zero-trust approach, regardless of whether the user or device is inside or outside the network. Every access request is verified and authenticated, and gaining controls are enforced based on the principle of least privilege.
3. Access Control
In a traditional approach, gaining access is often based on a network location. Once the users and devices are inside the perimeter, they typically have access to a wide range of resources based on their network privileges.
In a zero-trust approach, access controls are determined by factors such as identity, device health, and context, rather than just network location. This ensures that users and their devices are only given access to the specific resources they require to carry out their tasks.
4. Network Architecture
Typically, traditional security architectures are based on a castle-and-moat model, where there's a strong focus on protecting the network boundary.
Zero Trust architectures are often decentralised and micro-segmented, with zero-trust security policies enforced at a granular level. This allows for more fine-tuned control and better isolation of sensitive assets.
5. Response to Breaches
In a traditional security perimeter, once an attacker breaches the perimeter defences, they may have relatively free rein within the network to steal data.
With Zero Trust, even if an attacker gains access to the network, their movement and activities are closely monitored, and access to data is restricted based on their behaviour and risk level.
Frequently Asked Questions
How does zero-trust security differ from outdated security practices?
Zero Trust advocates for continuous verification and access controls, regardless of user location, rather than implicit trust within the network.
What is the difference between Zero Trust and security in depth?
Zero Trust focuses on continuously verifying user identity and enforcing strict access controls to minimise the attack surface while security in depth emphasises layering multiple security measures to protect against a wide range of threats.
What is the difference between Zero Trust and perimeter-based security?
Unlike perimeter-based security, which relies on fortifying the network perimeter with firewalls and other defences, Zero Trust assumes zero trust both inside and outside the network perimeter, emphasising continuous verification and least privilege access.
Round Up
Both traditional and zero-trust approaches protect against cybersecurity threats. However, zero trust is more proactive and offers more granular security that is better suited to today's ever-evolving threat landscape.
Navigating the complexities of cybersecurity can be a challenging task for businesses. That's why partnering with trusted experts like Aztech is essential.
Aztech provides comprehensive security solutions tailored to meet the unique needs of your organisation.
With us, you can confidently implement cutting-edge security measures like zero trust security over the traditional perimeter approach and ensure seamless operations that offer peace of mind.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)






-1.png?width=536&name=Blog%20Hero%20Banners%20(2)-1.png)
